What Is DNS?
The Domain Name System (DNS) protocol keeps records of which domain names correspond to specific IP addresses. DNS enables you to browse the web by typing in regular URLs instead of IP addresses.

More About DNS
At its core, the domain name system (DNS) coordinates navigation across the web by linking the domain names people use to identify websites with the internet protocol (IP) addresses computers use to identify websites.
As such, DNS is pivotal to how we use the internet today.
So there’s a lot to learn if you want to understand what makes the domain name system tick.
This robust guide will cover top-level and deep technical topics that business website owners/managers as well as folks in IT, DevOps, or system administration should find helpful.
Now, let’s take a long walk through how DNS works, the details on DNS servers and zones, understanding queries and caching, and dealing with DNS errors and security.
What Is DNS?
The domain name system protocol keeps records of which domain names correspond with which IP addresses.
DNS enables you to browse the web by typing in regular URLs instead of IP addresses.
What Does DNS Do?
When a user enters a domain name in their browser’s address bar, DNS starts the process of translating it into an IP address.
For example, when a user types in www.google.com, DNS will look up google.com’s IP address in the DNS database and send it to the browser. The browser can then deliver the user the website they were looking for, nearly instantly.
As the ultimate facilitator, DNS is not only important for providing users with a convenient way to access the internet, but it also plays an essential role in ensuring security and reliability.
How Does DNS Work?
The process of the DNS taking you from entering a URL into your address bar and being directed to the intended website has a lot of steps, but it’s not terribly complex. And with the help of quick internet and smart caching, it can happen in a matter of milliseconds.
Here’s what’s happening behind the scenes in a recursive DNS query (recursive tends to be the go-to because it can be faster — we’ll discuss all the query types later):
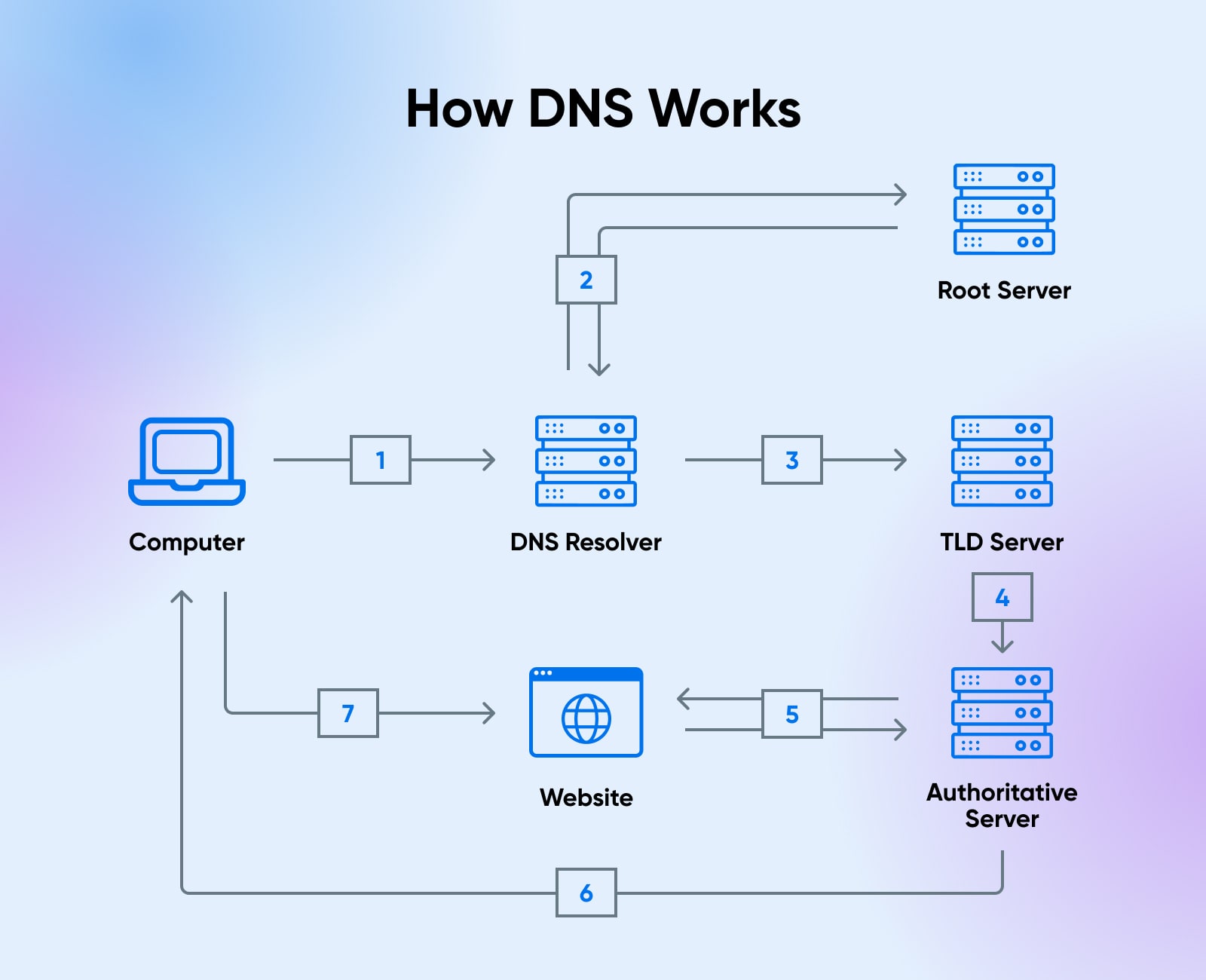
- It all starts when you (the DNS client) type or paste the domain name of a website into an address bar on a search engine. Because computers don’t use human language, this domain name has to be converted into an IP address in order for your computer to find it. So the computer immediately sends your request to a DNS recursive resolver for translation.
- First, the resolver goes to the root nameserver (FYI, some sources spell it with two words: “name server”) that aligns with the website’s top-level domain (TLD). The TLD is indicated by the domain extension — .com, .org, etc. Root nameservers keep lists of which authoritative nameservers align with which TLDs.
- Now that it knows where to go, the resolver visits the authoritative TLD nameserver that corresponds with that extension and begins looking for the specific IP address.
- Once it tracks the IP address down, the resolver passes it to the authoritative nameserver to be authenticated.
- The authoritative nameserver checks the IP address. Once it gets the expected response, it knows it’s found the website you’re looking for.
- The authoritative nameserver sends the confirmed IP address back to the web browser where this search first began.
- As soon as your web browser receives the IP address, the process is complete and the intended website will appear!
Yes, we dropped a lot of technical server terms on you in that above walkthrough. Keep reading if you’re interested in learning the details behind all of them.
Why Is DNS Important?
Today, finding whatever website we’re looking for across the internet is usually as simple as typing in a short URL.
That is due to DNS.
Without DNS, we would instead have to memorize and type in 12+ digit numbers to access the content we’re looking for.
And not just once.
Even if you were able to memorize the IP addresses of all the websites you visit in a day — which could be in the dozens or more for many of us — IP addresses change all the time due to server switches, internet service provider (ISP) updates, etc.
Thanks to DNS, the domain name can stay the same even when the IP address changes.
For website owners, DNS brings the flexibility to move between web hosting providers to improve speed or better align with their budget.
If we all had to re-memorize the digits to find our favorite online haunts every time they did this, imagine how that would hamper website traffic.
In this way, DNS is not only fundamental to a user-friendly internet for surfers and consumers, it’s also critical for businesses and anyone who uses a website to support themselves.
Deep Dive: What Is A DNS Server?
A DNS server is a computer that has a database full of public IP addresses and the domain names of the websites to which they link.
In other words, a DNS server is like a gigantic phone book where you “look up” an IP address. This happens when you type the name of the domain with which an IP address is associated into an address bar.
The DNS server kicks off the DNS workflow we explained above to make the correct domain name-IP address connection. From there it sends that info to the browser you’re using. The browser uses the address it’s provided to connect with the website’s content delivery network (CDN) edge servers or origin servers. When contact is established, the website can load and be accessed.
Again, this impressive process happens so quickly that, with a fast internet connection, it feels practically instantaneous.
Related: What Is A CDN?
Core Types Of DNS Servers
In fact, there are actually several different DNS server types that come into play to get your intended website loaded in front of you during a recursive DNS query.
If you feel solid in your understanding of DNS and really want to dig into the nitty gritty of DNS servers, then let’s explore the technicalities of each:
DNS Recursive Resolvers
Sometimes referred to as just DNS recursor or DNS resolver in the context of DNS servers, the DNS recursive resolver starts the DNS resolution process by receiving queries in the browser.
You can think of it as a librarian who has been asked to locate a specific book — thus kicking off a search process.
Root Nameservers
A root nameserver is a type of nameserver that lives in the DNS root zone. We’ll discuss more on zones shortly, but basically the root zone is the top of the DNS hierarchy and it holds the domain names and numeric IP addresses for all TLDs (reminder — those are .com, .org, etc.).
The root nameserver takes the query from the DNS recursive resolver and returns the appropriate authoritative nameserver for the top-level domain associated with the domain name.
Continuing the library example, it’s an index that helps the librarian identify which section to look in for a specific book.
TLD Nameservers
Top-level domain nameservers host all the IP addresses associated with different TLDs.
These TLDs are managed and delegated by the Internet Assigned Numbers Authority (IANA) and are generally used to categorize websites according to their purpose or location.
There are several categories of TLDs, including:
- generic TLDs (gTLDs): .com, .org, .net
- country-code TLDs (ccTLDs): .uk, .ca, .fr
- new TLDs (nTLDs): .agency, .bio, .charity
The TLD system helps to make the internet more organized and user-friendly by providing a clear structure to domain names.
Additionally, many TLDs are reserved for specific purposes or industries, such as .edu for educational institutions and .gov for government organizations. Overall, the TLD system plays a crucial role in how we navigate and interact with internet resources daily.
The TLD nameserver is comparable to the librarian arriving at the section of books to which the index pointed. Now they can begin looking for the book (aka the IP address).
Authoritative Nameservers
An authoritative nameserver is the authority in its given zone. It will contain records associated with specific domains (.org, .edu, and so on) and is responsible for providing IP addresses corresponding to those domains. Authoritative nameservers have the final say in determining the IP address associated with a given domain name.
Authoritative DNS nameservers are crucial for maintaining the integrity and accuracy of the DNS system, as they are the primary source of information about domain name registrations. They are typically managed by the organizations or individuals who own the domains and are responsible for ensuring that the DNS records associated with their domains remain accurate.
When a browser receives an IP address from an authoritative server, it can connect directly to that website without further assistance from the DNS system.
The authoritative nameserver is the space on the shelf where the book (the IP address) lives. If the book is available, the librarian can grab it and complete their quest.
Advanced Reading: What Are DNS Zones?
Ready to gain even more depth?
Then let’s explore the zones that make up DNS’ hierarchical structure.
Warning: This is an intricate breakdown of the ins and outs of DNS zones. You won’t need to know this information to run your business website, but if you’re a technical professional in IT, DevOps, or system administration you may find it helpful.
That said, let’s start off with the basics.
A DNS zone is a space for hosting DNS records for a particular domain. A DNS zone can contain various DNS record types, including SOA records (who is responsible for the domain), NS records (the authoritative server for the domain), and A records (the IP address connected to the domain).
Now, let’s get into all the types of zones!
Root Zone
The root zone is the topmost level in the hierarchical structure of the DNS. It consists of a set of 13 root servers distributed throughout the world, each managed by a different organization.
Root servers are responsible for managing domain name requests for all top-level domains. They receive requests from web browsers and then direct them to authoritative nameservers based on their geographical location or other criteria.
Forward Lookup Zones And Reverse Lookup Zones
Forward lookup zones contain records associated with specific domains. They can provide IP addresses corresponding to those domains when requested by web browsers.
And reverse lookup zones work the opposite way. When given an IP address, they can provide the domain name associated with it.
Reverse lookup zones are thought of and used less often, but they are necessary in some applications such as email providers, which rely on reverser lookup files to check for spammers.
Reverse lookup zones can also be used by network administrators to troubleshoot network connectivity issues, identify potential security threats, and monitor network traffic.
Stub And Secondary Zones
Stub zones enable administrators to perform quicker DNS name lookups by providing a copy of the authoritative zone file from another server. This helps to improve speed as well as reliability when resolving domain names.
Secondary zones provide redundancy for primary DNS servers by creating read-only copies of the authoritative zone files. These can be used in case of failure or downtime, so in a way they also promote speed and reliability.
Primary Zone
The primary zone (formerly known as the master zone) is the main authoritative source of information for a given domain. It contains all the records associated with that domain, its IP address, and other DNS settings.
The primary zone is managed by the organization or individual responsible for maintaining that domain’s DNS records. It’s important that this zone be kept up to date to ensure users are able to quickly access the domain.
When changes are made to a primary zone, those changes will propagate throughout the rest of the DNS, ensuring that everyone can access websites and online resources without issue.
Further reading: The Website Owner’s Guide To DNS Propagation
Secondary Zone
The secondary zone (sometimes called secondary master zone) is a backup authoritative source of information for a given domain. It contains all the records associated with that domain, its IP address, and other DNS settings and is used to provide redundancy in case of failure or downtime on the primary zone.
The secondary zone can be managed by either the same organization or individual responsible for maintaining the primary zone, or it can be delegated to another party. This helps to ensure that changes made to one server will propagate throughout the rest of the DNS quickly and accurately, thereby providing an additional layer of reliability and access.
Forwarder Zone
A forwarder zone is a special type of DNS server that forwards requests to other DNS servers. This helps reduce latency and improve reliability when resolving domain names, as the request is sent directly to another authoritative server instead of being routed through multiple servers.
Forwarder zones are often used by network administrators to quickly resolve and load domains. They can also be used in conjunction with secondary zones, as they provide an additional layer of redundancy for primary DNS servers in case of failure or downtime.
What Is A DNS Query?
We’ve thrown the term “query” around a bit so far — why not dig into exactly what that means?
“Query” tends to mean a question or request in the tech space. In the context of DNS specifically, a DNS query is a demand for information that goes from the DNS client to the DNS server.
Typically the goal behind a DNS query is to identify the IP address linked to a domain name.
Now that that’s out of the way, let’s chat about different types of DNS queries.
DNS Query Types
A recursive DNS query, or lookup, is where the originating DNS server (client) goes through a waterfall-like process of communicating with several other servers one after the other to find and return the right IP address.
In an iterative DNS query, the client server communicates directly with each of the DNS servers in the process all at the same time. This can also be called a non-recursive query.
Because the naming is similar, It’s critical to point out the difference between recursive DNS queries and the recursive DNS servers we talked about earlier.
The request sent to the DNS resolver that has to be, well, resolved is the query.
The computer that receives the recursive query and processes the response is the DNS resolver. The DNS resolver begins the sequence of queries that leads to a URL being turned into an IP address.
With an uncached DNS query — more on caching next! — there will probably be both recursive and iterative queries. However, you may see servers default to recursive queries more often due to the increased resolution speed.
What Is DNS Caching?
DNS caching is when the DNS server temporarily stores recently used DNS records to reduce page load time.
Related: What Is Cache?
By temporarily storing recently used DNS records in a cache, the DNS server can quickly respond to queries for domain names.
However, it is important to note that outdated or poisoned cache entries (which use false info to load the wrong websites — also known as spoofing) can cause issues with DNS, so regular checks should be done to ensure that the cached data is accurate. Additionally, security measures such as encryption and authentication protocols can help protect against malicious attacks on cached data.
Toward the end of this guide, we’ll go over more security specifics. But for now, let’s cover caching in more detail.
Browser DNS Caching
DNS records are cached by default by most modern web browsers, for a predetermined period of time.
This serves to reduce the number of processing steps required to check the cache and send the proper requests to an IP address. The browser cache is the first place that is searched when a DNS record request is performed.
Operating System DNS Caching
The DNS resolver at the operating system level is the last local place a DNS query searches for a record.
Operating systems are built to handle these local queries using something called a stub resolver. When a stub resolver gets a query, it dives into its own operating system cache for the record. If it can’t locate it, it goes on to send a DNS query beyond the local network.
How Do I Fix The “DNS Server Not Responding” Error? (Beginner To Advanced Tips)
The “DNS server not responding” error message is something you may have run into before.
This message indicates that either your browser is unable to establish a connection to the internet, or the DNS server can’t connect to a correct IP address.
Often, the breakdown is on the user end, so here are some tricks you can try to get you re-connected to the website you’re trying to visit.
Keep in mind that these tips get progressively more technical as they go. If you get to a point where you no longer feel comfortable making changes on your own, get with your IT team if you have access to one, your hosting provider, or in some cases your ISP to troubleshoot together.
Use A Different Browser or Device
Here’s an easy one. Simply try another browser or switch to a whole new device (tablet, smartphone, etc.) if you’re having trouble connecting with a specific domain.
Sometimes the issue just needs a moment to correct itself, so this gets you to the content you need while the DNS takes a second to reset.
Try Restarting
The number of times “unplug it and plug it back in” advice works in the tech world is high.
Restarting everything is the equivalent of that.
To see if the issue is with your operating system, restart your computer in safe mode.
If that doesn’t work, it could be your modem or router. Restart each of these to clear the cache and possibly resolve your DNS connectivity breakdown.
After this, the troubleshooting advice gets a little more advanced.
Shut Off Anything That Could Interfere
As necessary as it is, unfortunately security software such as a firewall program can get in the way of your internet access.
To see if that’s what’s causing the disconnect, simply turn off these kinds of programs for a moment and try again. If they’re consistently giving you trouble, it may be time to shop around for a new provider.
In addition, network connections may be interfering with the DNS server.
On a Mac computer, you can find a list of connections at System Preferences > Network. On Windows, visit Control Panel > Network and Internet > Network and Sharing Center > Change adapter settings.
Disconnect any you aren’t using and reload your browser page to see if that was the issue.
Clear The Operating System DNS Cache
To remove the previous DNS lookups that are hanging around in your operating system cache and that may be causing your DNS server connection issue, you can pretty quickly clear out the cache.
The easiest way to do this, no matter your device, OS, or version is to use a “system cleaner” tool like BuhoCleaner or CCleaner. Just read the reviews and check out the website for any tool you use to make sure you aren’t downloading anything dangerous.
Turn Off IP Version 6
There’s a known issue with internet protocol version 6 (IPv6) — the current iteration of internet protocol at the time of this writing — that it can throw the “DNS server not responding” error.
Disabling IPv6 might help you resolve this error. There are different ways to do this depending on the operating system and device. Comparitech has a helpful guide.
Check For Network Connectivity
Now we’re getting into more technical territory — it’s time to check for network connectivity issues that could be causing DNS resolution to fail.
This can be done by running network diagnostic tools (this list may help you get started) to check for packet loss, latency, and other issues that could cause DNS resolution to fail.
Additionally, you should verify that the DNS server is reachable and that there are no network configuration issues preventing communication with the DNS server.
Verify DNS Records And Domain Name Matching
You can also check to verify that the DNS records match the domain name.
Do this by running DNS lookup tools (here’s a simple one) to check for the presence and accuracy of DNS records.
Incorrect DNS records can cause DNS resolution to fail, so it’s important to ensure that the records are correct. You should also verify that the domain name matches the IP address associated with it, as mismatched records can cause DNS resolution to fail.
Learn more about accessing your domain’s DNS records in Nameservers Vs. DNS: A Complete Guide.
Check DNS Resolver And Authoritative DNS Server Functionality
Next, check the functionality of the DNS resolver and authoritative DNS servers.
You can do this by running tests such as ping and traceroute to check for network connectivity and DNS resolution. If the tests fail, it could indicate that there are issues with the DNS resolver or authoritative DNS server.
Manually Change Your DNS Server
Your home network usually works with the same DNS server, as configured by your ISP. If your usual server isn’t responding, you won’t be able to connect to the internet.
So, you need to change your DNS server.
First, find a free, public DNS server address, Cloudflare and Google Public DNS offer good options.
On Mac, add a new DNS server at System Preferences > Network > primary network connection > Advanced > DNS.
On Windows, type “ncpa.cpl” in the Windows search box. When it pulls up, right click on your network > Properties > Internet Protocol Version 4 > Properties.
Select Obtain an IP address automatically and Use the following DNS server addresses. Enter your new DNS server address(es) and check Validate and OK.
Restart your internet after this switch.
Update The Network Adapter Driver
DNS server connection failure may potentially be caused by an out-of-date network adapter driver.
You can update your driver yourself or use a program to help. If you aren’t familiar with the ins and outs of driver software, we don’t recommend you try to do this process on your own.
Instead, find a service like Driver Booster or Driver Easy to help you download, install, and automatically maintain the appropriate drivers for your computer.
By following these steps, you should be able to identify and resolve DNS issues that may be causing problems with domain name resolution.
Steps You Should Take For DNS Security
Did you know that in addition to its primary function of converting domain names into IP addresses, DNS also plays a crucial role in security?
That’s because DNS can be used to block or redirect malicious traffic, protecting users from phishing attacks and malware infections. It can also be used to implement content filtering policies, blocking access to certain websites or types of content.
A secure DNS infrastructure is essential for protecting online data. So we’re going to guide you through several steps you should implement to create a secure DNS environment.
Note that this is another one of those sections where we’ll dip in and out of complex ideas and technical terms (DNS isn’t the lightest topic, is it?!). If you own or run a business website and you want to ensure DNS security but aren’t an IT, DevOps, or system administration pro, it’s likely you’ll need some input from one.
To make sure your DNS security is all squared away, you can share this section of the article with your security professional. If you don’t have one, your hosting company is likely a good resource. If your hosting provider doesn’t offer the support you need, it may be time to think about managed hosting from a company with professional website experience and expertise.
Ok, now let’s get those safeguards rockin’!
Overview: DNS Hardening
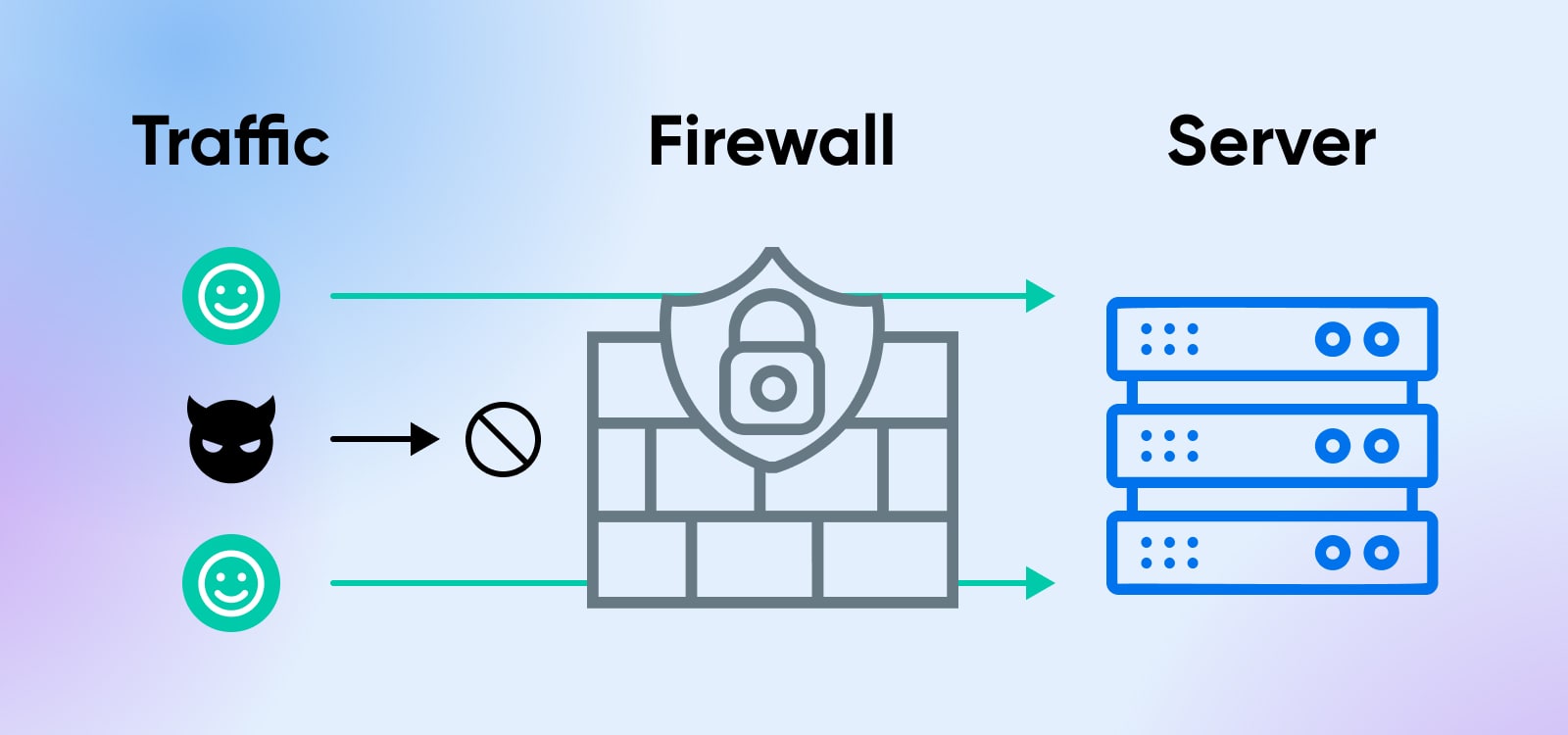
DNS hardening refers to the process of securing the DNS infrastructure to prevent attacks and ensure the availability and reliability of domain names.
This involves implementing security measures such as access control, encryption, firewalls, and monitoring to protect against common DNS attacks like DNS spoofing, DNS cache poisoning, and distributed denial of service (DDoS) attacks.
DNS hardening also involves regularly updating and patching DNS software and configurations to prevent vulnerabilities from being exploited. By hardening the DNS infrastructure, organizations can reduce the risk of DNS-based attacks, maintain the confidentiality and integrity of their data, and ensure the availability of their online resources.
DNS hardening is an essential part of any comprehensive cybersecurity strategy, and the following steps can help increase security hardness and prevent costly breaches and downtime.
Zone Transfer Encryption And Monitoring
Getting more specific, zone transfers are a critical aspect of DNS management that enables the replication of DNS data between primary and secondary nameservers.
Zone transfers are crucial in ensuring the availability and reliability of domain names by allowing secondary servers to obtain updated DNS information from primary servers.
However, zone transfers can also pose security risks if not properly secured, and malicious actors can exploit vulnerabilities in zone transfer configurations to gain unauthorized access to DNS data.
To mitigate these risks, as part of DNS hardening organizations should implement access, encryption, and monitoring measures to protect zone transfer communications and prevent unauthorized access.
Regularly reviewing and updating zone transfer configurations is also essential in preventing vulnerabilities from being exploited and ensuring the integrity, confidentiality, and availability of DNS data.
DNSSEC Implementation
DNSSEC is an important security protocol that helps protect domain names from malicious attacks. It provides an additional layer of security to the DNS infrastructure by digitally signing and authenticating DNS data, ensuring that it has not been tampered with or spoofed.
By implementing DNSSEC, organizations can ensure the integrity, confidentiality, and availability of their online resources and prevent costly breaches resulting from DNS-based attacks.
Additionally, DNSSEC enables secure zone transfers between primary and secondary nameservers which are essential for maintaining the reliability of domain names.
DNSSEC is a detailed element of the DNS hardening world. If you want to learn more about what a security professional might do to get DNSSEC running on your site, read this guide from Cloudflare.
Caching Server Restrictions And Protections
As we discussed earlier, caching servers are an essential component of the DNS infrastructure that helps speed up the domain name resolution process by caching frequently-accessed domain name records.
However, caching servers can also pose security risks if not properly protected. Malicious actors can exploit vulnerabilities in caching server configurations to launch DNS-based attacks like cache poisoning or amplification attacks (a type of DDoS attack that overwhelms a system with traffic).
To handle these risks, organizations can harden their DNS security efforts by implementing strict access control policies to restrict access to caching servers, monitoring and updating caching servers’ software and configurations, and implementing encryption protocols to secure caching server communications.
Malicious Domain Blocking
Malicious domain blocking is a preventative hardening measure used to protect against DNS-based attacks that involve malicious domains. These attacks aim to redirect users to fraudulent web pages or steal sensitive information by exploiting vulnerabilities in DNS configurations.
Malicious domain blocking involves analyzing DNS traffic and identifying domains that are known to be associated with malicious activity, such as phishing, malware, or spam. Once identified, these domains are added to a blacklist, and any DNS requests to these domains are simply blocked or redirected to a safe page.
You Don’t Have To Deal With DNS Alone
Not only is DNS foundational to the way we use the internet today, as you can see there are tons of highly-technical, always-moving parts beneath the surface that keep it running smoothly.
If you’re running into DNS issues that are impacting your website or need help working through DNS security concerns, DreamHost’s managed hosting and website management pro services are here to take the technical work off your plate so you can focus on the things you actually love about running a website.