Last month, a mid-sized e-commerce company lost everything. Their hosting provider, a budget option with impressive marketing,disappeared overnight after a ransomware attack. No backup recovery. No support response. Just a blank website and three years of customer data, gone.
Stories like this shouldn’t still happen in 2025, and yet they do.
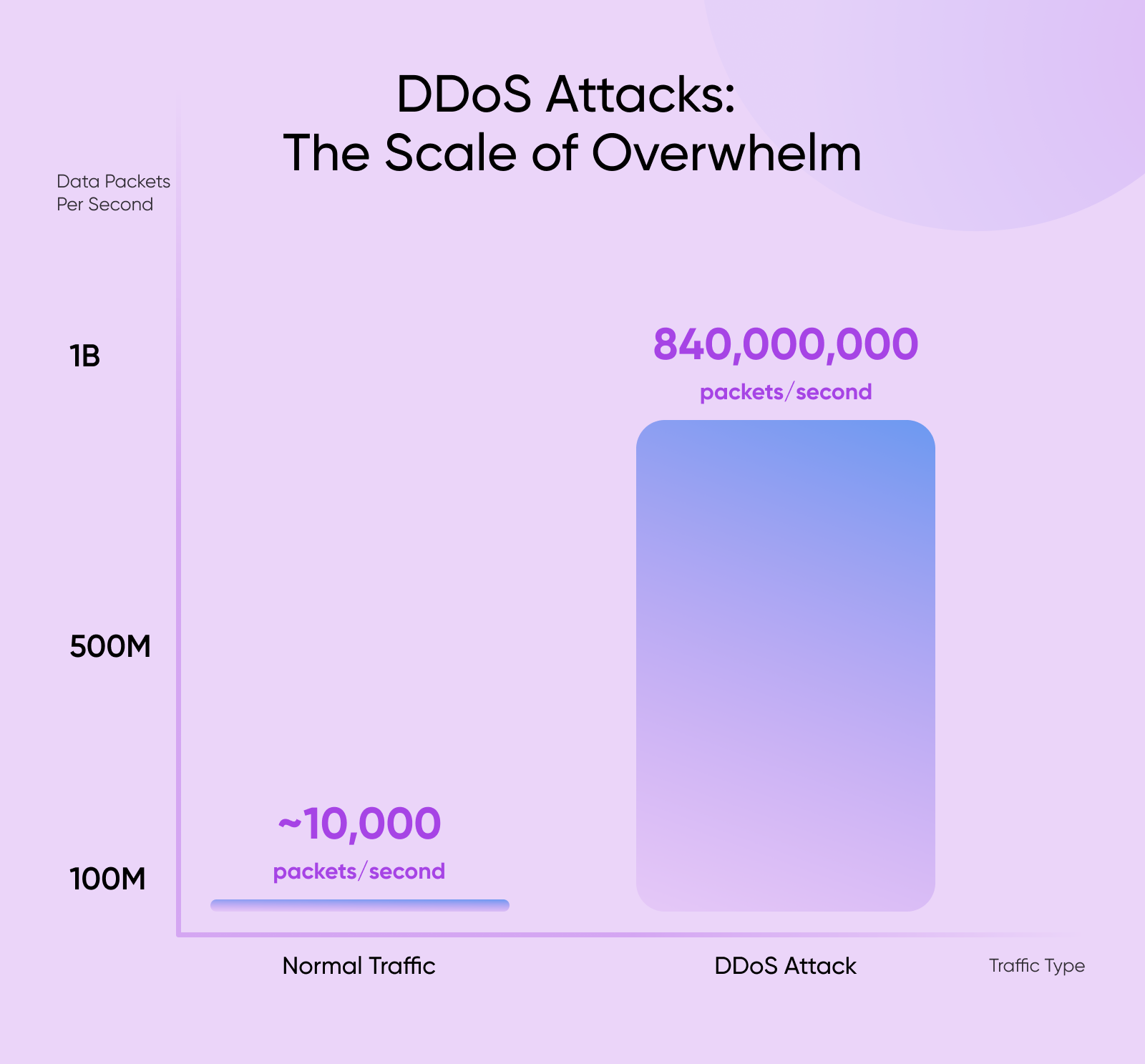
The hosting industry faces security threats that are evolving faster than any single company can handle alone. DDoS attacks now reach 840 million packets per second, overwhelming even major infrastructure providers.
DDoS Attack
DDoS means Distributed Denial of Service. It’s an attack that tries to make a system or network unavailable by flooding it with traffic from multiple sources.
Read MoreRansomware gangs target hosting companies specifically, knowing one breach can affect thousands of websites. And for every established hosting provider working to maintain high standards, there are dozens of fly-by-night operators racing to the bottom on price, cutting corners on security, and putting their customers at risk.
Here’s the problem that keeps me up at night: how does a small business owner know which hosting provider they can actually trust?
Traditional signals don’t work anymore. Marketing claims are easy to make, and testimonials can be manufactured.
Even price isn’t a reliable indicator —expensive doesn’t guarantee quality, and cheap doesn’t always mean cutting corners. The hosting industry has never had a standardized way for customers to verify that their provider follows basic security and operational standards.
Until now, every hosting company has faced these challenges alone. We’ve each built our own security protocols, developed our own abuse response procedures, and tried to stay ahead of threats independently.
But the internet doesn’t work in isolation, and neither should the companies that host it. That’s why DreamHost joined the Secure Hosting Alliance as a founding member —and why we spent the last year working with industry peers to build something bigger than any single company could create on its own.
Related Post: [STUDY] 12% of Small Businesses Say They’ve Paid a Ransom Demand
The Verification Vacuum and Why Trust Matters More Than Ever
Too many hosting providers prioritize short-term profits over long-term reliability. They offer rock-bottom prices, make promises they can’t keep, and often lack the infrastructure or expertise to handle security threats. Some disappear entirely when problems arise, leaving customers with no recourse.
These kinds of providers persist because the hosting market has spent decades competing primarily on price. When customers can’t easily verify quality differences between providers, price becomes the deciding factor. This creates a race to the bottom that rewards the cheapest option, not the most secure or reliable one.
The consequences for businesses are real and devastating:
- Lost data means lost revenue, lost customer trust, and sometimes lost businesses entirely.
- Extended downtime during critical launches or sales periods costs thousands of dollars per hour.
- Security breaches expose customer information, creating legal liability and reputational damage that takes years to recover from.
- Poor abuse response gets your site caught in spam blacklists or malware warnings, destroying your search rankings overnight.
But how do you, as a business owner, know if a hosting provider has genuine abuse mitigation procedures or just marketing copy? How do you verify they’ll respond to abuse reports, maintain your uptime, and handle government data requests lawfully?
Before the Secure Hosting Alliance’s certification program came along, you couldn’t. There was no standardized certification, no industry-wide verification system, and no way to independently confirm that you were choosing a hosting provider that followed basic security and operational standards.
Other industries have solved this problem —you look for security badges when shopping online, trust seals from payment processors, and certifications from financial institutions. Healthcare providers display their accreditations.
But hosting? We’ve been operating in a trust vacuum, asking customers to take our word for it.
That had to change. The hosting industry needed a way to make trustworthiness visible and verifiable — not just claimed, but demonstrated and independently certified.
The Secure Hosting Alliance: A Collaborative Approach
The Secure Hosting Alliance launched about a year ago as an initiative of the Internet Infrastructure Coalition (i2Coalition). The i2Coalition formed during the 2011 fight against SOPA and PIPA legislation, and is the leading voice for companies that build the Internet’s infrastructure.

The SHA represents growth in the coalition’s activities, focused around reactive policy defense, to now include proactive industry improvement. Rather than waiting for problems to force change, a number of hosting providers and affiliated companies came together to establish standards defining what responsible hosting actually means.
To date, 26 online service providers have become Secure Hosting Alliance Certified. Certificants include major players across the hosting spectrum. DreamHost, Automattic, Hostinger, BigScoots, and GoDaddy, just to name a few.
4 Key SHA Goals
The SHA exists to transform how the hosting industry operates. We’re working toward four interconnected goals that address the industry’s most pressing challenges.
1. Develop a cooperative framework for fraud prevention and abuse response.
Security threats don’t respect company boundaries. When one hosting provider gets exploited for phishing or malware distribution, it damages trust in the entire industry.
The SHA creates channels for member companies to share threat intelligence, coordinate takedown responses, and work effectively with law enforcement. This collaboration makes all of us more effective at protecting customers.
2. Establish common industry standards for privacy, security, and transparency.
For too long, “secure hosting” has meant whatever each company wanted it to mean. The SHA’s certification program defines specific, measurable standards around transparency, infrastructure misuse protocols, network reliability, and government request handling that customers can rely on. These are concrete operational requirements that certified providers must demonstrate and maintain.
3. Create a unified language and taxonomy for the web hosting industry.
When every company uses different terms to describe similar services or security measures, customers can’t make meaningful comparisons. Standardized terminology makes it easier for customers to understand what they’re buying.
It also helps the industry coordinate on shared challenges, because clear definitions enable better communication between providers, law enforcement, and regulators.
4. Contribute to legislative and regulatory discussions with informed industry perspectives.
Lawmakers and regulators often lack technical understanding of how hosting infrastructure actually works. When they try to solve legitimate problems, like online abuse or data protection, without industry input, they risk creating regulations that sound good but don’t work in practice. The SHA gives policymakers access to collective industry expertise.
These four goals work together to create an environment where responsible hosting providers can thrive — customers can make informed choices, and the entire Internet infrastructure becomes more resilient.
The Trust Seal: Making Trustworthiness Visible
The SHA Trust Seal is where all this work becomes tangible for customers. It’s the visible symbol that a hosting provider has been independently verified to meet rigorous operational, security, and ethical standards.
Think of it like the security badges you see when checking out online, or the certifications displayed in a doctor’s office.
The hosting industry has never had this.
Earning SHA certification isn’t automatic, even for founding members who helped create the standards. Each hosting provider must demonstrate compliance across four interconnected pillars. The certification process involves documentation review, policy verification, and ongoing accountability to maintain the seal.
The Four Pillars of SHA Certification
SHA certification evaluates hosting providers across four critical operational areas:
| Pillar | What It Requires | Why It’s Important |
| Transparency | Clear, publicly accessible policies including Acceptable Use Policy, terms of service, and documented operational procedures. | Customers know exactly what rules apply, what to expect, and how the provider operates. |
| Infrastructure Misuse Protocols | Documented contacts and response procedures with prioritized handling of confirmed abuse reports and security threats. | When security issues arise, they get addressed quickly and professionally rather than ignored or delayed. |
| Network Resource Reliability | Proactive monitoring, comprehensive recovery planning, and capacity management to ensure consistent uptime. | Your website stays online when you need it, backed by documented disaster recovery and redundancy. |
| Government Request Handling | Lawful, well-documented procedures for handling data requests that protect user rights while meeting legal obligations. | Your data gets the due process protection it deserves, with clear policies on when and how information is disclosed. |
Why DreamHost Joined the SHA
When we first heard about the Secure Hosting Alliance and its goals, my immediate reaction was straightforward: “None of this is new for us.” They were advocating for hosts to adopt policies that reflect how DreamHost has done business for the last 25 years. Signing on was a no-brainer. But that’s only part of the story.
We joined the SHA as a founding member for three reasons:
1. Security threats require collaborative solutions, not individual heroics
When malware spreads through compromised hosting accounts or phishing campaigns exploit lax security at one provider, it damages customer trust across all hosting services.
We can build the most robust security infrastructure in the world at DreamHost, but if customers can’t tell us apart from a less trustworthy operation, we’re all competing in a race to the bottom.
The SHA working group meets monthly to discuss security trends. When one member identifies a new attack vector or discovers a particularly sophisticated fraud operation, everyone benefits from that knowledge.
2. Independent ownership gives us the freedom to prioritize industry health
DreamHost has always been independently owned. We don’t answer to investors demanding we maximize quarterly earnings. That independence means we can participate in initiatives like the SHA because they’re the right thing for the industry and our customers.
Many hosting providers operate as subsidiaries of larger technology conglomerates or private equity portfolios. Those ownership structures create pressure to focus on individual company performance rather than industry-wide improvements. We don’t face those constraints.
3. Charter member status gave us a voice in defining “secure hosting”
Standards created without input from companies that actually operate hosting infrastructure tend to be either too vague to mean anything or too rigid to work in practice. We spent months in working group sessions with engineers, security professionals, and operations leaders from other founding members.
We hammered out requirements that would be both rigorous and achievable.
What specific response time should abuse reports require? How do you document government request handling procedures in ways that protect customer privacy while remaining legally compliant? What does “proactive monitoring” mean in concrete terms?
The SHA transforms “trust us” into “verify us.”
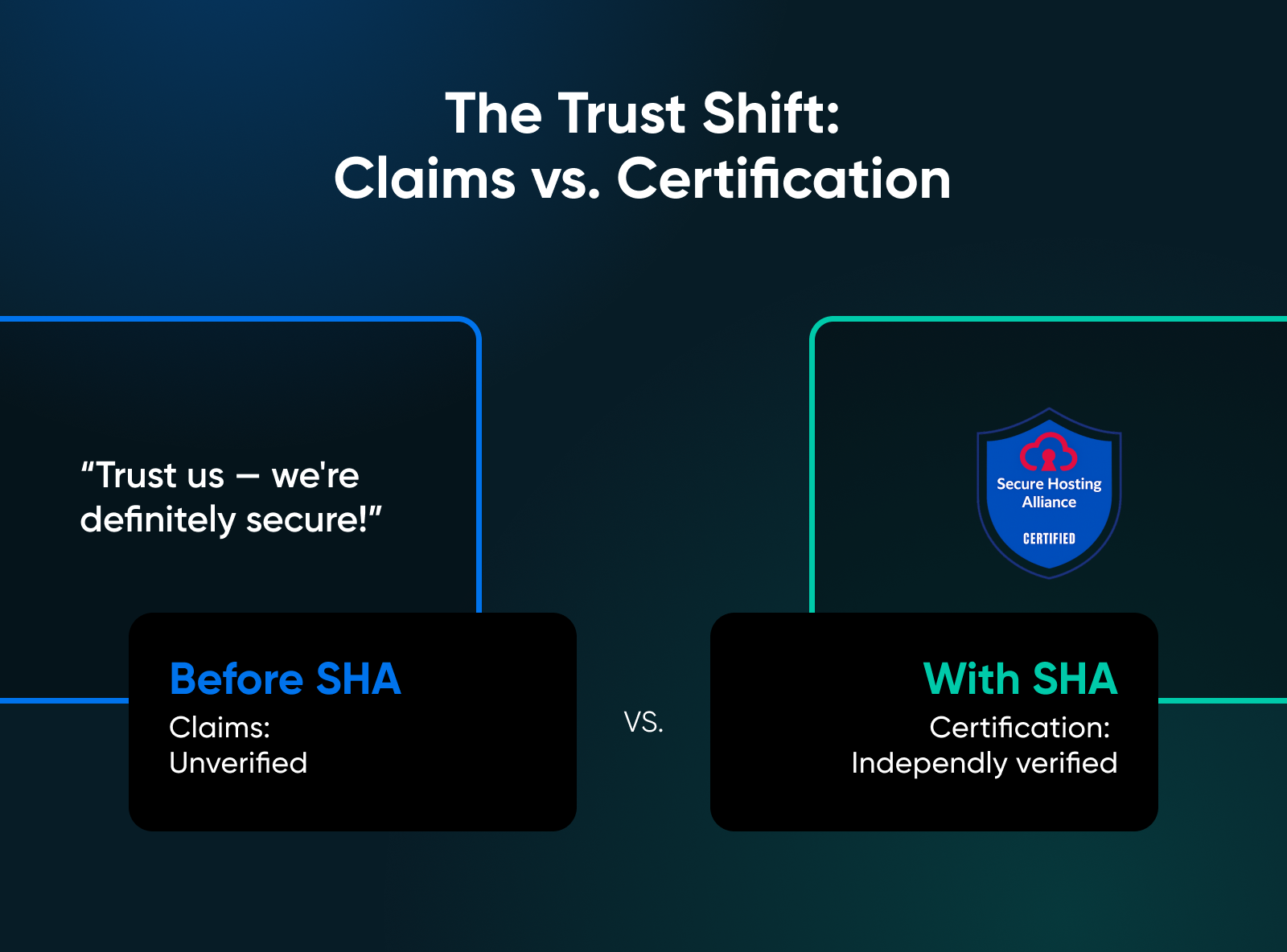
Instead of comparing marketing promises, customers can compare certifications. Instead of hoping a provider follows good security practices for WordPress hosting, they can verify it through a SHA certification.
DreamHost is SHA certified, validating practices we’ve maintained throughout our history. But the certification itself isn’t the achievement we’re most proud of. It’s the collaborative framework we helped build that will raise standards across the entire industry. That’s the real value of the Secure Hosting Alliance.
Related Post: DreamHost Achieves Secure Hosting Alliance Certification
Looking Ahead to the Future of Secure Hosting
The SHA Trust Seal isn’t a finish line, but a starting point for continuous improvement in how the hosting industry protects customers and maintains trust.
We continue attending monthly SHA working group meetings that give us insight into attacks targeting other providers before they reach our infrastructure. They help us respond faster when threats do emerge. This monthly coordination with industry peers represents a fundamental shift in how hosting security works.
Hosting security has always required collaborative solutions. Individual companies, no matter how large or well-resourced, can’t solve ecosystem-wide challenges alone.
When you see the SHA Trust Seal on a hosting provider’s website, you’re seeing proof of ongoing accountability. You’re seeing transparent policies, responsive abuse handling, reliable infrastructure, and lawful data protection.
The SHA provides standards, certification, and ongoing accountability. The rest is up to us — hosting providers willing to meet those standards, and customers willing to prioritize verified trustworthiness over the lowest price.
Learn more about the Secure Hosting Alliance and its certification program at hostingsecurity.net.

