The term “cloud computing” gets thrown around a lot these days. But what does it really mean? Behind the buzzword lies real technologies, like infrastructure-as-a-service (IaaS), that provide scalable on-demand computing, storage, and networking.
However, migrating to the cloud is like moving your organization into an infinitely scalable yet invisible office tower. 75% of the businesses state that over 40% of their data stored in the cloud is sensitive. Neglecting security here leaves a lot of company information vulnerable to threats, like unauthorized access, exploits, and non-compliance.
The good news is that while “the cloud” seems ephemeral, with the right foundations and best practices, you can effectively secure IaaS environments.
In this guide, we’ll share 12 essential tips to lock down security on your unmanaged cloud servers, VMs, containers, storage, and services, benefiting from the fast growth that cloud environments offer. Let’s get started.
1. Disallow Root Password Logins
One of the most common methods that attackers use to gain unauthorized access to servers is by brute forcing weak passwords for highly privileged accounts like root or administrator.
To understand why, imagine yourself as a malicious hacker. If your goal is to get into a system and gain access to sensitive data, you would likely start by attempting to brute-force the root password (repeatedly trying different passwords until the correct one is found). If the attempt is successful, you gain access to the root account, which has the highest level of system permissions available, allowing complete control over the server.
The thing with brute force attacks is this: weak passwords can be cracked easily with the right tools— and even strong passwords can be cracked by a patient, determined hacker.
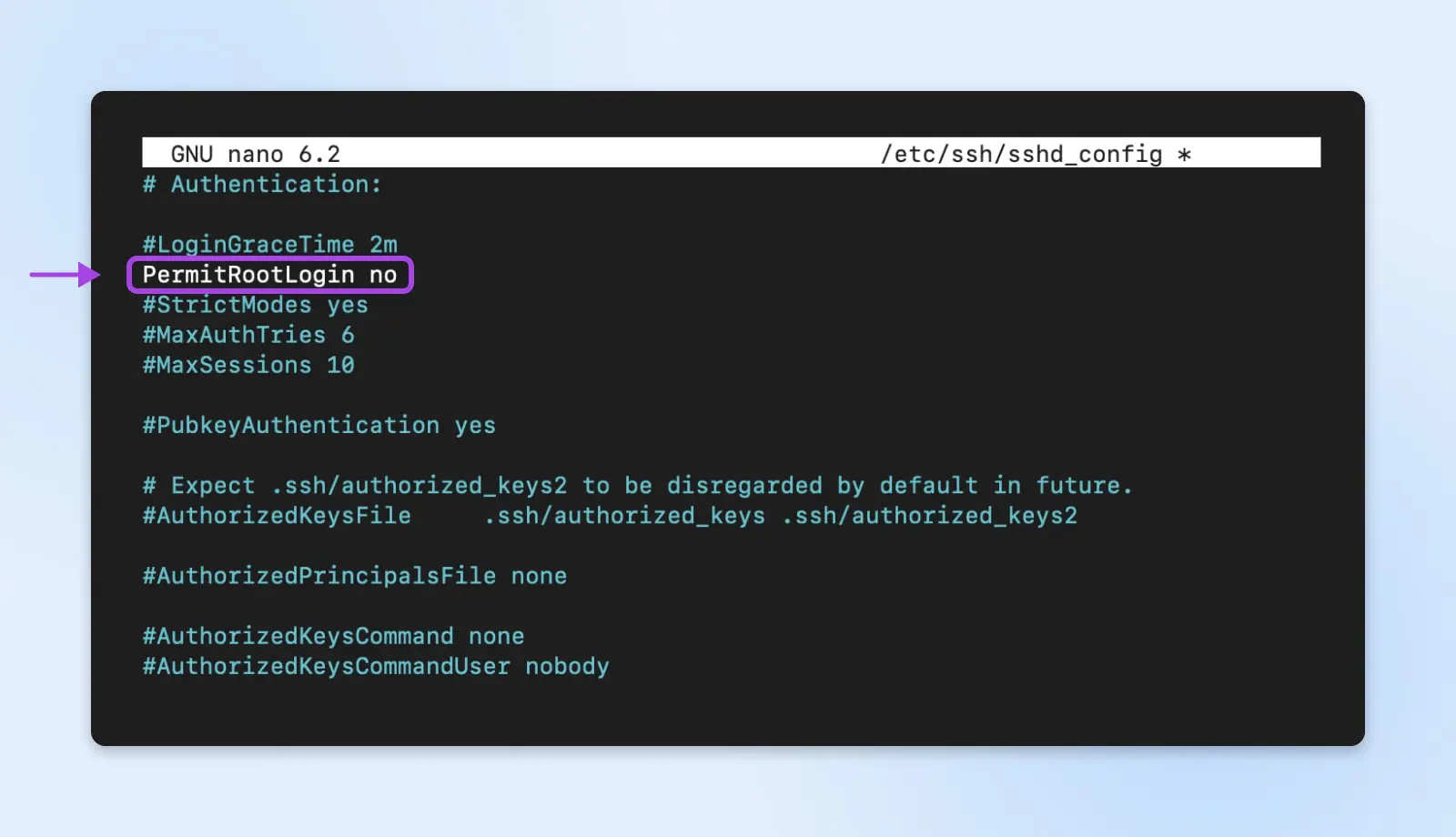
What if you completely disable password-based root login and instead rely on SSH key-based authentication as an alternative?
SSH
Secure Shell Protocol (SSH) is a cryptographic network protocol for running services securely through an unsecured network. It is mostly used for command-line executions and remote logins.
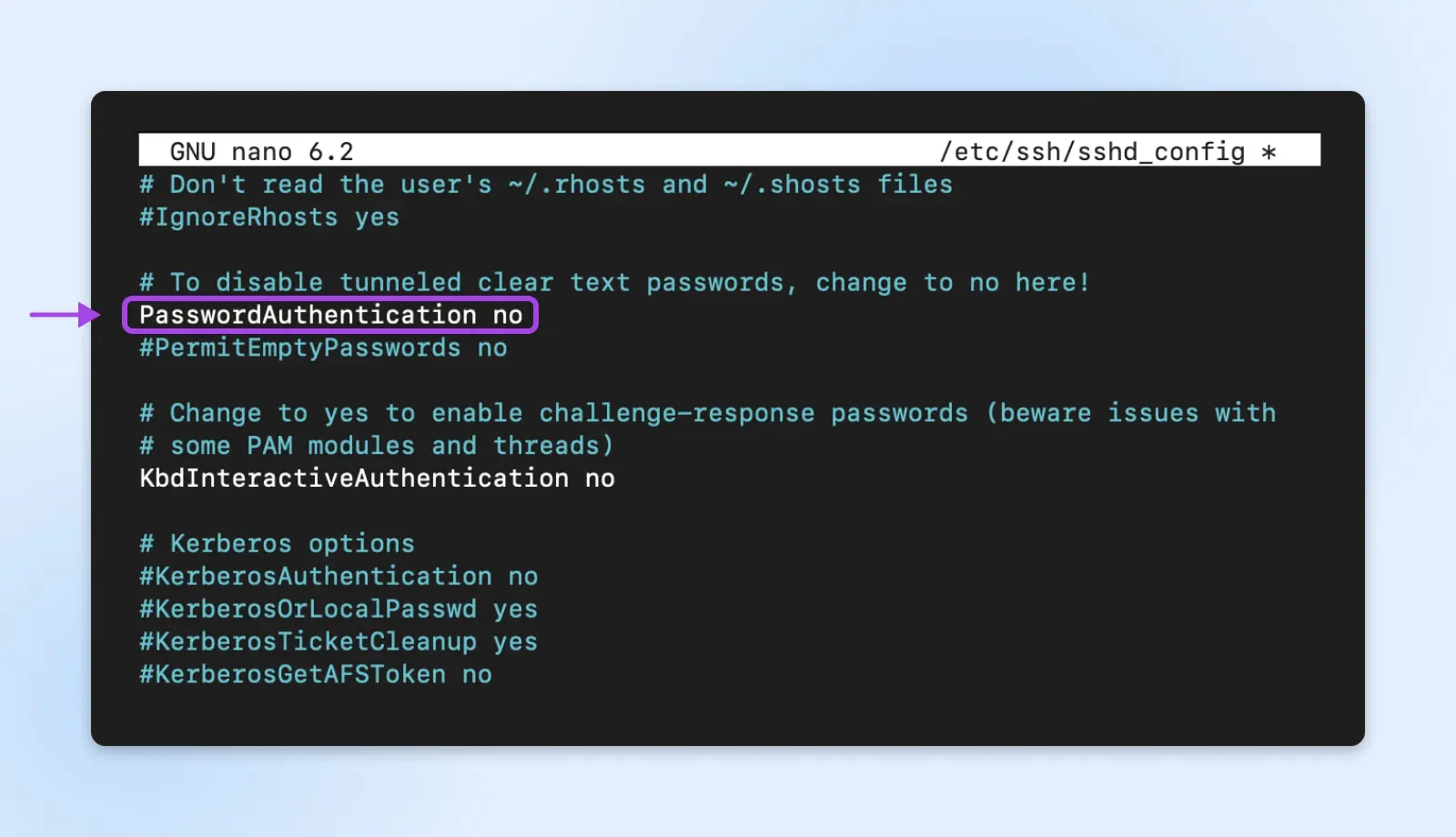
Read MoreThis configuration can be found in the /etc/ssh/sshd_config file on your Linux server.
This is an excellent step in the right direction. SSH keys use asymmetric encryption, meaning a private and public key pair – rather than a password – is used to authenticate login attempts.
You can go a step further and disable root login over SSH to prevent people from attempting brute-force on root. This can be done by changing the PermitRootLogin to no in the same file.
The private key, as the name implies, is kept privately by the authorized user and stored on their computer. The corresponding public key is then stored on the server associated with that user’s account.
During the login process, the keys use cryptographic methods to validate the authorized connection without revealing the actual private key. This method effectively protects against brute force attacks since the login cannot be compromised through mere password guessing.
2. Enable Automatic Security Upgrades
All software contains vulnerabilities: some known and some yet undiscovered.
Attackers are constantly probing programs for new bugs that allow them to gain access and control. When vulnerabilities are found and fixed by the software vendors, they publish security updates.
If you’re manually upgrading systems, hackers may use the opportunity where your systems are still vulnerable and gain access. But with auto upgrades, you can leave that stress behind.
For example, if a vulnerability is discovered in a programming library used by your cloud database software (e.g., SQLite), hackers could soon learn of it and launch attacks. But if your database servers are set up to automatically install security updates as they are published, it will download and apply the patch to fix the issue before any compromise occurs.
Also, the process of auto-upgrades can be customized to apply security patches on a set schedule only after they have been adequately tested. For mission-critical systems, you may choose to stage and test updates before broad deployment. Automation removes the burden of manual intervention while still keeping your cloud access secure.
3. Install And Configure Fail2ban
Brute force attacks come in many forms, targeting various network services. Beyond abusing logins like SSH, we also need to consider web applications, email servers, databases, and more, which may be vulnerable to password-guessing attempts.
This is where intrusion protection tools like Fail2ban come in very handy.
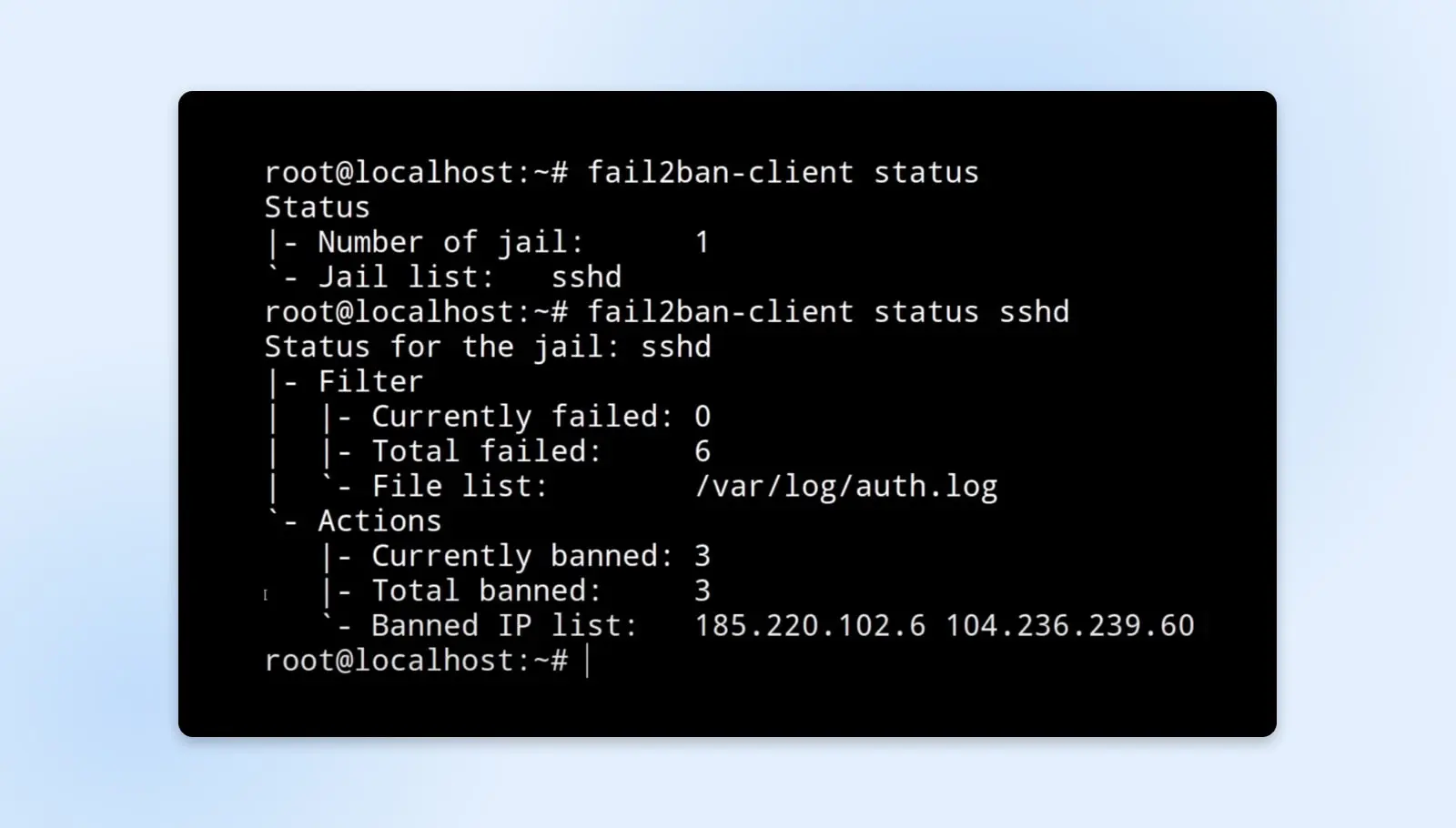
Fail2ban works by continuously monitoring log files generated by network services and parsing them for signs of repeat failed access attempts that are indicative of automated brute forcing. When failed attempts exceed a configurable threshold, Fail2ban will automatically update system firewall rules to block the source IP address responsible, preventing further abuse of that service.
To put this in perspective consider this:
Alice configures Fail2ban on her web server to monitor authentication failure logs. If an IP makes five failed login attempts to the admin console in under two minutes, indicating a potential attack, Fail2ban will automatically block that IP from accessing the web application for 10 minutes. This protects the availability of the app for legitimate users while deterring malicious actors.
The temporary IP bans can help slow down attackers actively trying to guess credentials or find exploits. Fail2ban is highly customizable as well — you can fine-tune the services monitored, thresholds before banning, duration of bans, logging parameters, and more. This flexibility allows it to be extensively leveraged to protect against brute-force risks across most cloud workloads.
4. Configure Cloud Security Groups As Firewalls
While tools like Fail2ban operate at the individual server level to protect against attacks, we must also consider safeguarding cloud resources at the network layer. Cloud platforms at DreamHost are pre-configured to be secure.
Along with this, DreamHost provides you with a configurable virtual firewall so you can decide what traffic is accepted or rejected apart from the default settings.
For example, web servers typically only need to accept inbound HTTP and HTTPS connections over ports 80 and 443. So, the security group assigned to these hosts would be configured to block all other protocols and port combinations via deny-by-default rules. Similarly, outbound traffic would be narrowed down to only what is absolutely essential for that function.
Careful configuration of security groups acts as the first line of defense, allowing only authorized ingress and egress traffic to reach your cloud servers and services according to best practices of least privilege access.
5. Consider Implementing An Intrusion Detection System
While we have discussed measures to proactively block unauthorized access attempts and prevent exploitation of known vulnerabilities, skilled attackers may still find ways to penetrate defenses through as-yet-unknown flaws.
In these cases, detection as early as possible becomes critical.
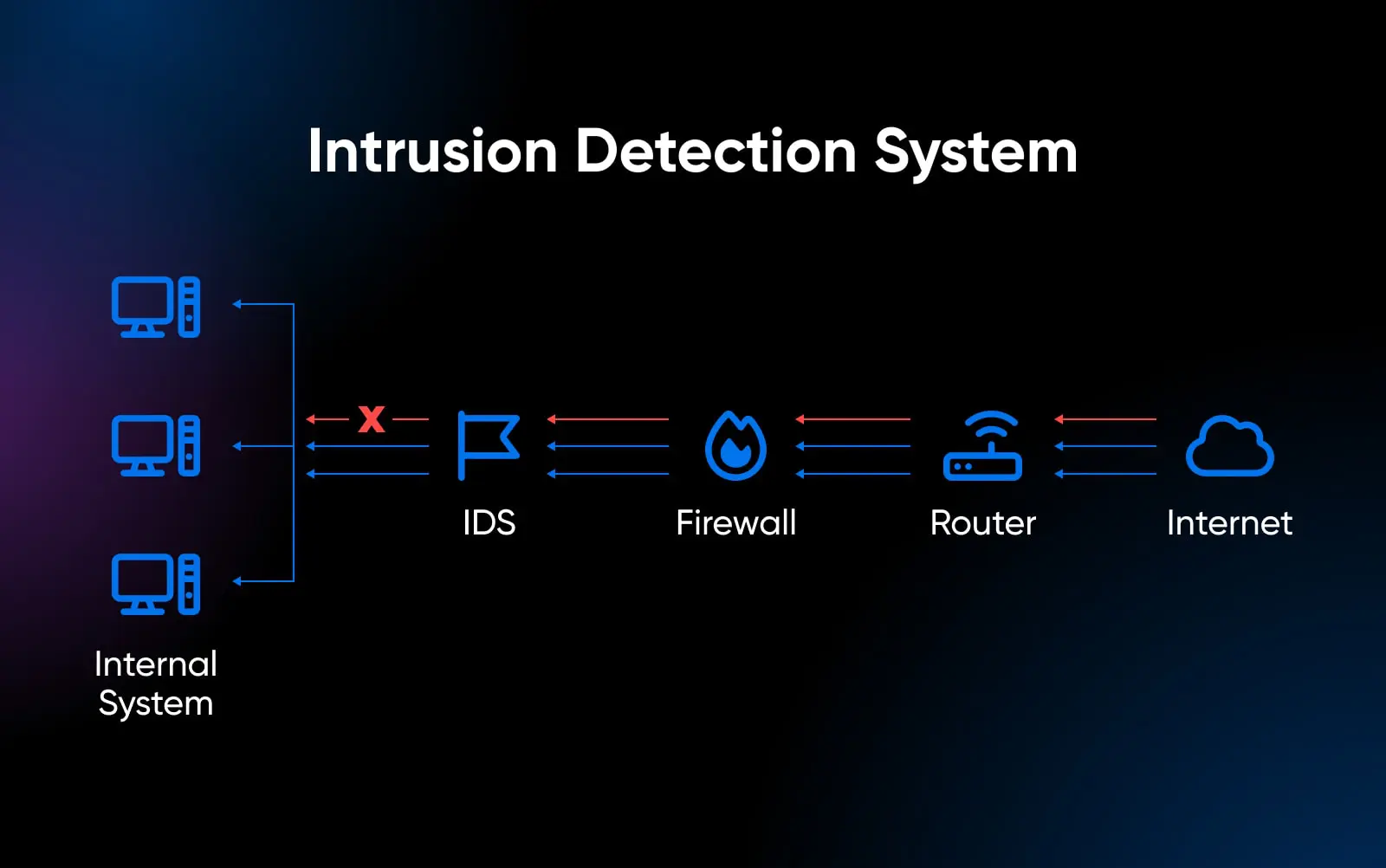
This is where an Intrusion Detection System (IDS) can provide immense value — continuously monitoring systems for suspicious activities indicative of a breach. IDS solutions come in two main forms:
- Network IDS (NIDS): Analyzes network packets inspecting for malicious payloads like viruses or known attack patterns. Often used to detect malware propagation and network-focused hacking attempts.
- Host IDS (HIDS): Monitors activities, configurations, and logs on an individual server. Checks for signs of tampering, unauthorized changes, or integrity violations.
“To prevent brute-force attacks, multi-factor authentication, secure session policies, rate limiting, automatic timeouts and a well-rounded intrusion detection system (IDS) should be implemented. Also include the use of secure and random session identifiers, storing session data in secure locations like HttpOnly and Secure cookies, and implementing mechanisms to detect and prevent unauthorized session access.”
— Jesse Befus, Managing Director, Enterprise Identity & Access Management at ATB Financial
A popular example used for Linux environments is Tripwire. It maintains an extensive baseline database of file attributes like permissions, hashes, metadata, registry entries, and more for the host. At periodic intervals, it compares the current state against this baseline to check for any unauthorized modifications that could indicate foul play.
For example, an attacker exploits a vulnerability to get shell access on one of the web servers. He attempts to replace website files with a malicious version that steals customer payment data. As soon as this alteration is made, Tripwire detects the change during its next scheduled integrity check. It alerts the administrator about the unexpected webroot modification, allowing them to investigate the breach before major damage occurs.
Without Tripwire, such an attack may have gone unnoticed allowing the attacker to stealthily collect customer records over an extended period. Intrusion rapidly detected is intrusion rapidly contained!
As they say, “prevention is ideal but detection is a must,” and that’s where cloud IDS offerings deliver immense value to keep your data secure.
6. Leverage Data Encryption Extensively
Thus far we have discussed multiple layers of security controls with the goal of preventing unauthorized access to your cloud servers. However, a fundamental data security tenet is that prevention may fail, but encryption serves as a last line of defense.
Even if all other safeguards are bypassed and cloud servers get successfully breached, encryption ensures stored data like SQLite databases, archives, and file shares remain protected and unusable to attackers. This applies to data-in-transit as well which should be encrypted during flows across networks.
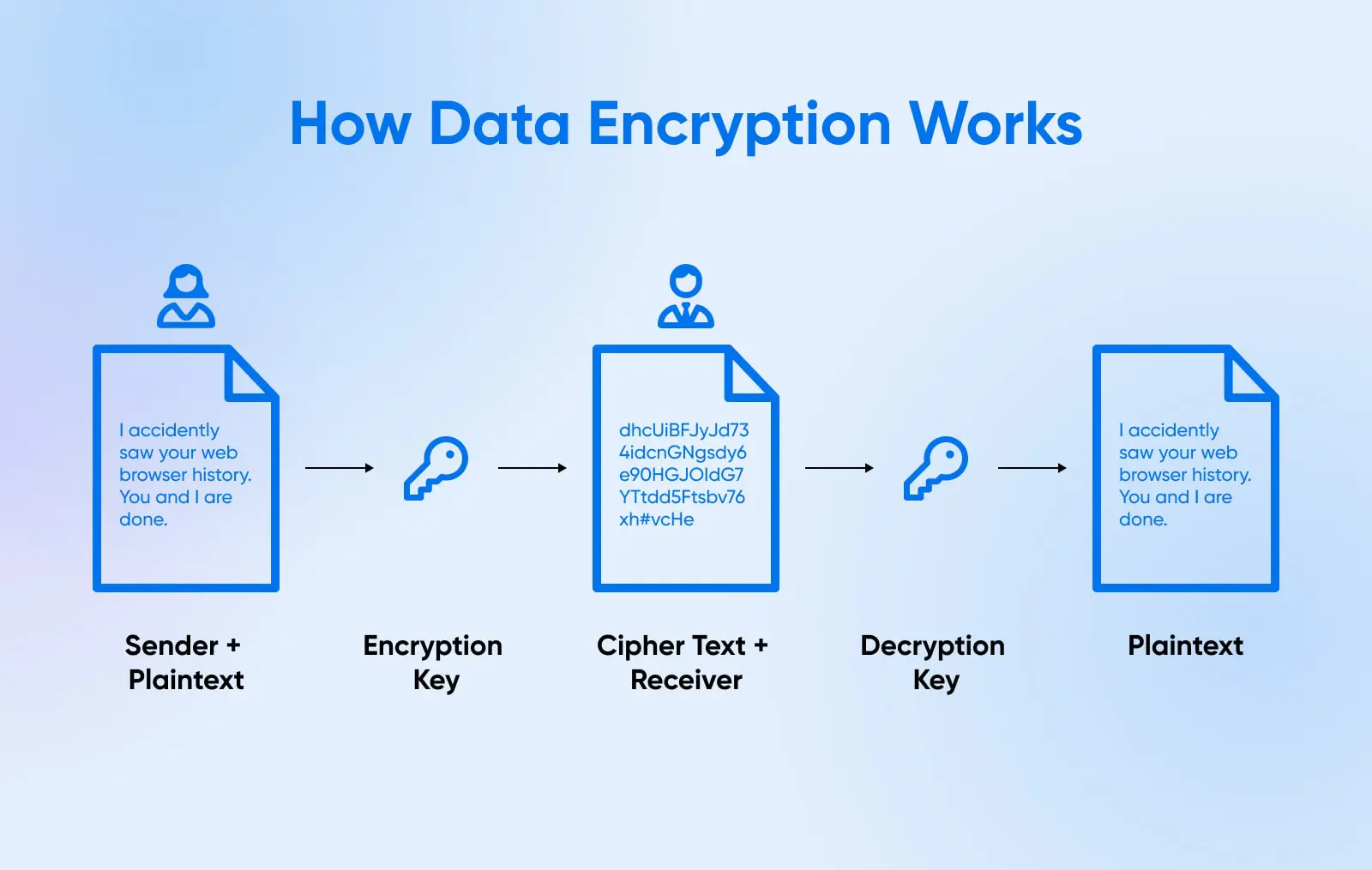
Encryption broadly falls into two categories:
- Asymmetric: Uses a public/private key pair where anything encrypted with the public key can only be accessed via the matched private key and vice versa. Generally used for secure connections.
- Symmetric: A shared secret key is used to encrypt and decrypt data. Used for efficient bulk encryption of data at rest as the same key encrypts/decrypts.
If all other defenses fail, encrypted data foils the attacker’s goals. What good is breaching a cloud database server if all records are gibberish without the decryption key?
7. Schedule Regular Security Audits
We have now covered various preventative and detective controls to secure cloud infrastructure and data at rest. However, an overlaying practice that connects the dots across all of them is routine security audits.
76% of the surveyed companies follow a regular security audit protocol to be proactive about security issues.
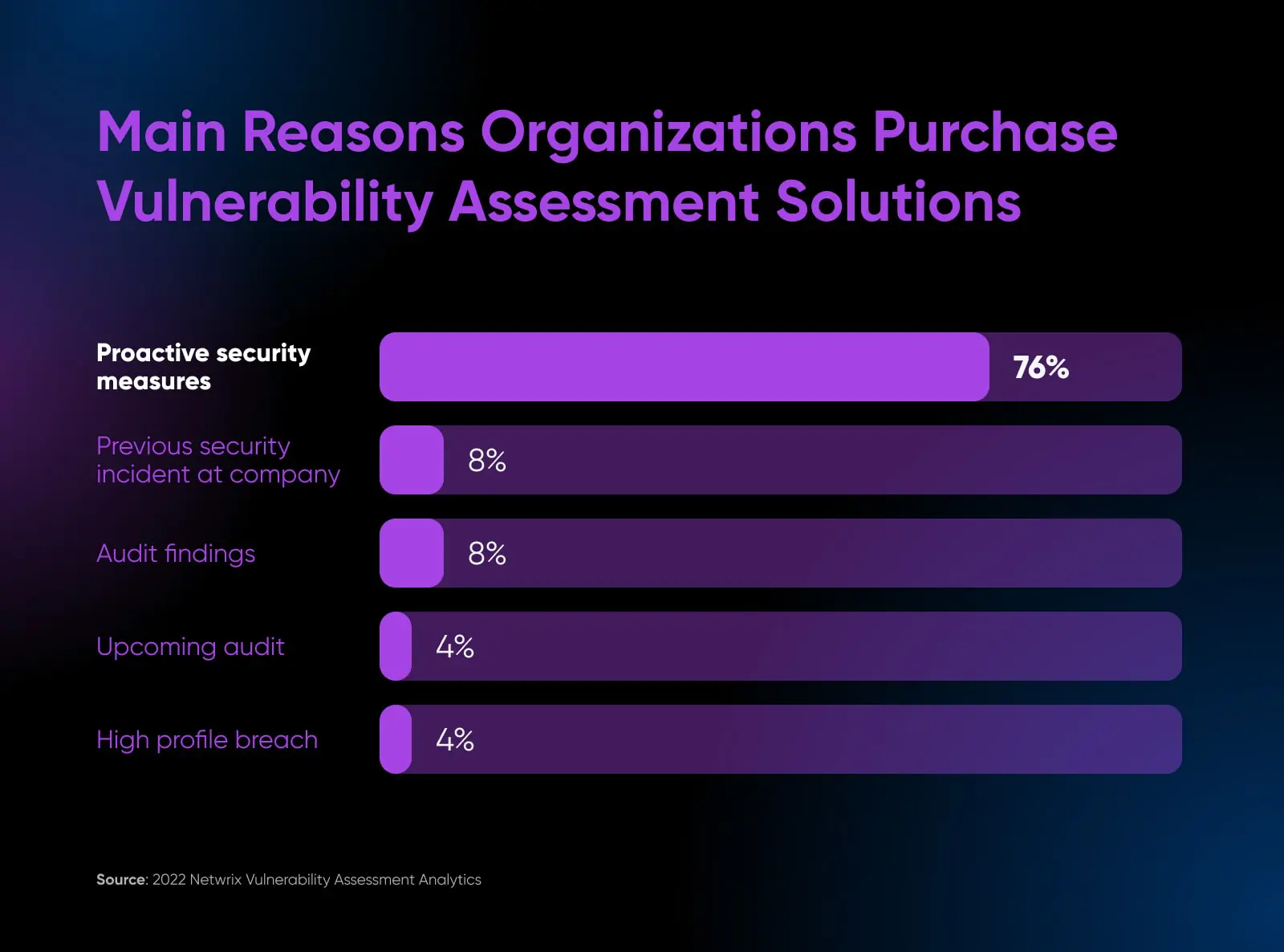
Audits serve several invaluable purposes:
- Validate that controls are properly implemented as intended.
- Identify if any deficiencies or gaps need improvement.
- Quantify and prioritize residual risk exposures.
- Uncover unknown vulnerabilities not visible otherwise.
- Provide an updated snapshot of current security posture.
Basically, audits tell if your documented cloud practices accurately reflect reality.
You can implement informal self-serve audits as part of daily administration or schedule exhaustive formal assessments annually depending on program maturity.
Think of these routine cloud security audits as necessary “health exams” that find risk areas and validate successful practices so corrective actions can be taken before something goes wrong.
8. Implement Identity And Access Management
Now that we have discussed safeguards deployed directly within the cloud infrastructure itself, the next logical layer we progress to is managing administrative access.
Without identity and access management (IAM) acting as cloud gatekeepers, attackers would simply target user credentials next to bypass infrastructure defenses through legitimate access channels.
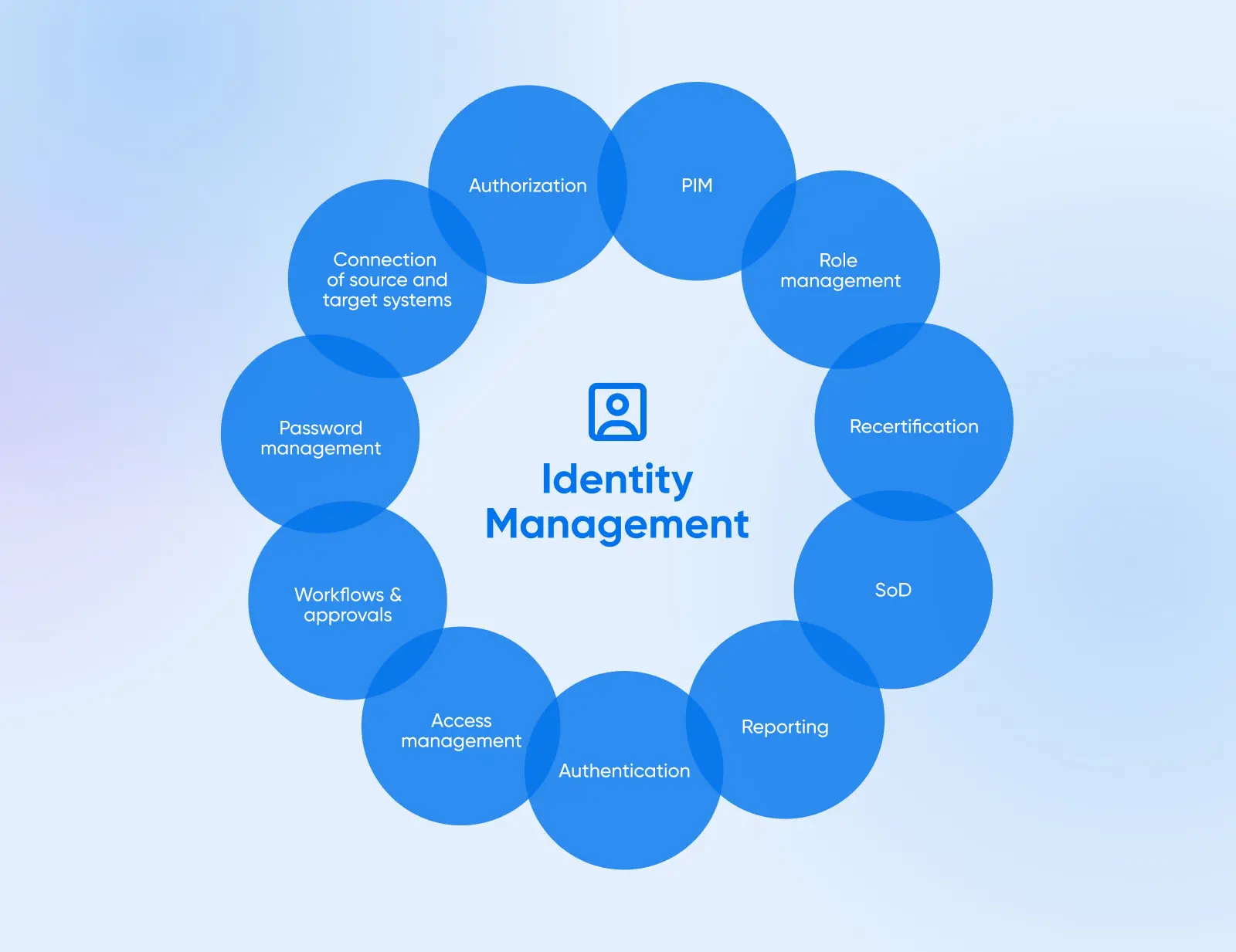
That’s why a robust IAM program becomes the foundation for who can access cloud environments and data within prescribed permissions — granting only essential privileges.
Some of the most important components of an IAM include:
- Central directory services: Maintain user accounts and roles in a central directory like Active Directory with single-sign vs. locally on individual servers. Enforces access revocation, password policies, and consolidation.
- Principle of least privilege: Users are matched to roles and groups that map to the smallest subset of systems and permissions needed for function vs. blanket access. Minimizes exposure blast radius if accounts are compromised.
- Strong authentication: Passwords augmented with multi-factor authentication to access cloud admin consoles and infrastructure. Reduces brute force susceptibility by necessitating additional factors like tokens or biometrics when authenticating sessions.
- Entitlement management: Access assignments and elevations tracked, providing visibility into permissions. Automated access reviews combined with routine entitlement reporting to prune unnecessary assignments over time.
- Audit logs: Activity logging with tools like CloudTrail that records admin actions across the cloud estate. Critical for incident investigation, compliance, and exposure of risky insider actions.
- API/tokens: Code-based cloud access via API and tools rely on short-lived generated tokens. Adds protections compared to just user-based interactive logins.
Robust IAM is critical to cloud system security because it dictates who can penetrate cloud environments regardless of infrastructure security defenses. Get IAM wrong and all your security measures may become vulnerable. But if you implement privilege access, backups, and encryption, the rest become exponentially more effective since IAM cuts off unauthorized entry at the roots.
9. Require Multi-factor Authentication (MFA)
Expanding further on access controls, one incredibly useful mechanism to incorporate is multi-factor authentication (MFA) enforcing multiple methods of verifying identity.
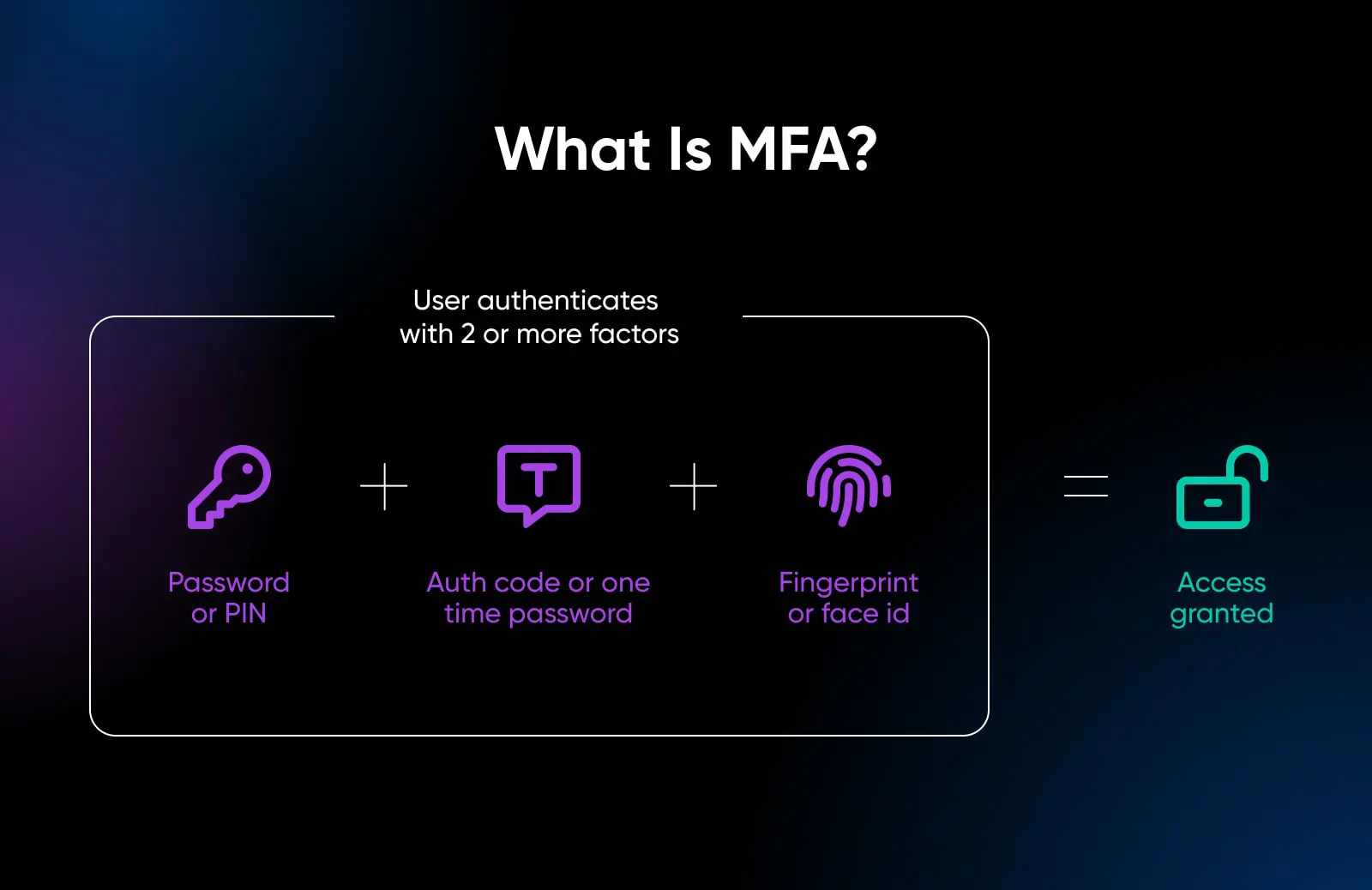
Where single-factor authentication relies on just one credential, like passwords, MFA capitalizes on users having multiple validation methods in their possession by requiring any two or more to fully authenticate sessions. This minimizes impersonation risks substantially, even if one factor is compromised.
Common examples include:
- Requiring a one-time verification code sent via SMS/email along with username/password entry.
- Using a hardware token or authenticator app to generate rotating codes.
- Leveraging biometrics like fingerprint scans or facial recognition on mobile.
- Answering security questions preset by the user.
So even if a cloud console password is guessed correctly via brute force, without intercepting the user’s phone for SMS tokens, the session cannot progress. This is why DreamHost accounts can be secured with MFA— This added barrier can deter automated attacks, leaving them looking for an easier target.
10. Secure Endpoints That Access The Cloud
Thus far our data protection techniques have centered on securing the cloud infrastructure itself as well as access channels into it. However, we need to consider threats that originate from compromised endpoints, which then connect to cloud environments.
If laptops and workstations lack anti-virus protections for example, malware could pivot from them into otherwise well-hardened cloud servers. That is why endpoint security safeguards integrate tightly with cloud access policies as another critical layer of defense-in-depth.
Common endpoint hardening techniques involve:
- Installing reputable anti-virus/anti-malware tools.
- Deploying endpoint detection & response (EDR) for additional monitoring.
- Enabling host-based firewalls and intrusion detection systems.
- Maintaining patching and security updates promptly.
- Tracking asset inventories with agent software.
- Prohibiting admin privileges on end user devices.
- Enforcing drive encryption via Bitlocker.
- Blocking unauthorized peripheral devices like USB storage.
- Securely configured web proxies and DNS filtering.
11. Prioritize Security Awareness And Training
After discussing the various technical and procedural safeguards to secure cloud data, we now touch upon what is often the biggest vulnerability: the human element.
As much as we architect layered defenses like firewalls, IAM, encryption, and hardening to protect cloud infrastructure, none of those matter if users themselves engage in risky practices whether intentionally or accidentally.
Some common examples include:
- Reusing passwords across personal and work accounts.
- Opening phishing emails and malicious attachments.
- Not vetting links before clicking them.
- Storing passwords in insecure files or notes.
- Discussing confidential data over insecure channels.
- Failing to logout of cloud service accounts after usage.
- Saving files containing sensitive data in public cloud storage buckets.
The list goes on. No technical controls can fully compensate for lack of security awareness among teams operating cloud platforms day-to-day. That makes ongoing education the strongest shield by cultivating a self-reinforcing culture of security.
Implement formal security awareness training programs should focus on:
- Simulated phishing: Trains staff to identify and avoid real world phishing lures targeting cloud credentials and data. Improves threat literacy.
- Secure practices: Provides guidance on password hygiene, social engineering red flags, handling sensitive data, proper cloud usage and more. Sets usage Expectations.
- Cloud risks: Highlights common cloud-specific vulnerabilities like misconfigurations, access creep and data leaks so staff better comprehend implications of their responsibilities.
- Compliance requirements: Outlines policies for access management, third parties handling data and utilization regulations. Maintains compliance.
- Incident reporting: Encourages confidential reporting of suspected violations or breaches spotted. Enhances visibility.
“No password, passkey, password manager, or two-factor authentication *alone* can protect you from social engineering. Social engineers target us as humans first and the technology we use second. We must understand that technical solutions alone are not going to provide perfect protection.”
— Dr. Martin Kraemer, Security Awareness Advocate, KnowBe4
Annual or bi-annual refresher training combined with continuous coaching nurtures a security-focused organizational culture where cloud users better appreciate safe data handling.
12. Monitor Service Provider Security Posture
Last but certainly not least, a dimension of cloud security that often gets overlooked is management of security provided by the cloud service provider itself.
“Monitoring is important as tools do not work 100% by itself. Have a third-party or a team to analyze alerts and respond to incidents. This is the best [way] to improve your security and safeguard your information assets.”
— Felipe Mafra, CISO North America at Thales GTS
While discussions around encryption, access management and the like focus on controls directly managed by us, the cloud provider also implements foundational protections for the data centers, networks and hardware infrastructure underpinning our computer environments.
Examples of security measures implemented by providers include:
- Physical data center protections like fences, video surveillance and guards.
- Biometric authentication for data center access.
- Redundant power and backups to secure infrastructure.
- Hardened hypervisors separating customer instances.
- DDoS mitigation for networks.
- Regular third party audits.
So while we govern security of the cloud workloads deployed, we must also periodically review security posture maintained by the service provider particularly relating to any shared responsibility areas.
You can start by:
- Reviewing provider audit certifications.
- Monitoring advisory notices for emerging threats impacting services.
- Examining provider employee screening and data handling policies.
Move To The Cloud Fearlessly, With DreamHost
Your data is your business. It’s the work that you’ve spent years building. That’s why it’s so important to keep your data secure, especially when it’s stored in the cloud. The ideas we covered in this article are an excellent starting point for your cloud-based data security.
But here’s the thing: keeping your data secure isn’t just about following a list of rules. It’s about being vigilant, about being aware of the risks, and about taking steps to protect yourself.
The truth is that data is as valuable as oil, and hackers want to steal as much as they can. And they’re only getting better at what they do. That’s why you also need a service provider that helps implement security best practices while you do what you do best — grow your business.
DreamHost focuses on security and backups, so you can rest assured that your valuable work isn’t in vain if a security incident does occur. If you’re considering a cloud service provider for your project, try DreamHost today.

DreamObjects is an inexpensive object storage service great for hosting files, storing backups, and web app development.
Try It Free for 30 Days
