DreamPress:
Managed WordPress Hosting
Hassle-free, high-performance WordPress to grow your business.
- Extreme Speed with Built-in Caching
- Powerful tools like Email, Staging & Backups
- Free Priority Site Migration (reg. $199)
- 24/7 Expert WordPress Support

Managed WordPress Hosting Plans
Fast, secure, and optimized for WordPress.
What DreamHost Offers


We’ll migrate your site for free!
You can request a free professional service or use our free automatic plugin to easily migrate any WordPress site to DreamHost yourself with no downtime. Choose your plan to get started on your migration!
Sign Up NowWhy pay twice as much?
There are a number of good managed WordPress hosts out there, but only DreamPress offers the powerful features, tools and support your business needs, AND at 1/2 the price of the other guys. Plus! We include email. Try us! Take advantage of our 30-day money-back guarantee.
Sign Up NowManaged WordPress Plans
Have lots of traffic or do you manage multiple sites? We'll design the perfect Managed WordPress solution to fit your goals and budget.
Sign Up NowThe Best Features Only on
DreamPress
1-Click Staging NEW
Confidently test new plugins, themes, and code before pushing your changes to your live site.
Bulletproof Backups
Easily protect and restore your site with access to automated and on-demand backups.
Built-in Caching
Get better results with a faster site — without all the extra work of implementing caching yourself.
We Make WordPress Easier for You
Leave migrating your site, installing WordPress, managing security and updates, and optimizing server performance to us. Now you can focus on what matters most — growing your business.
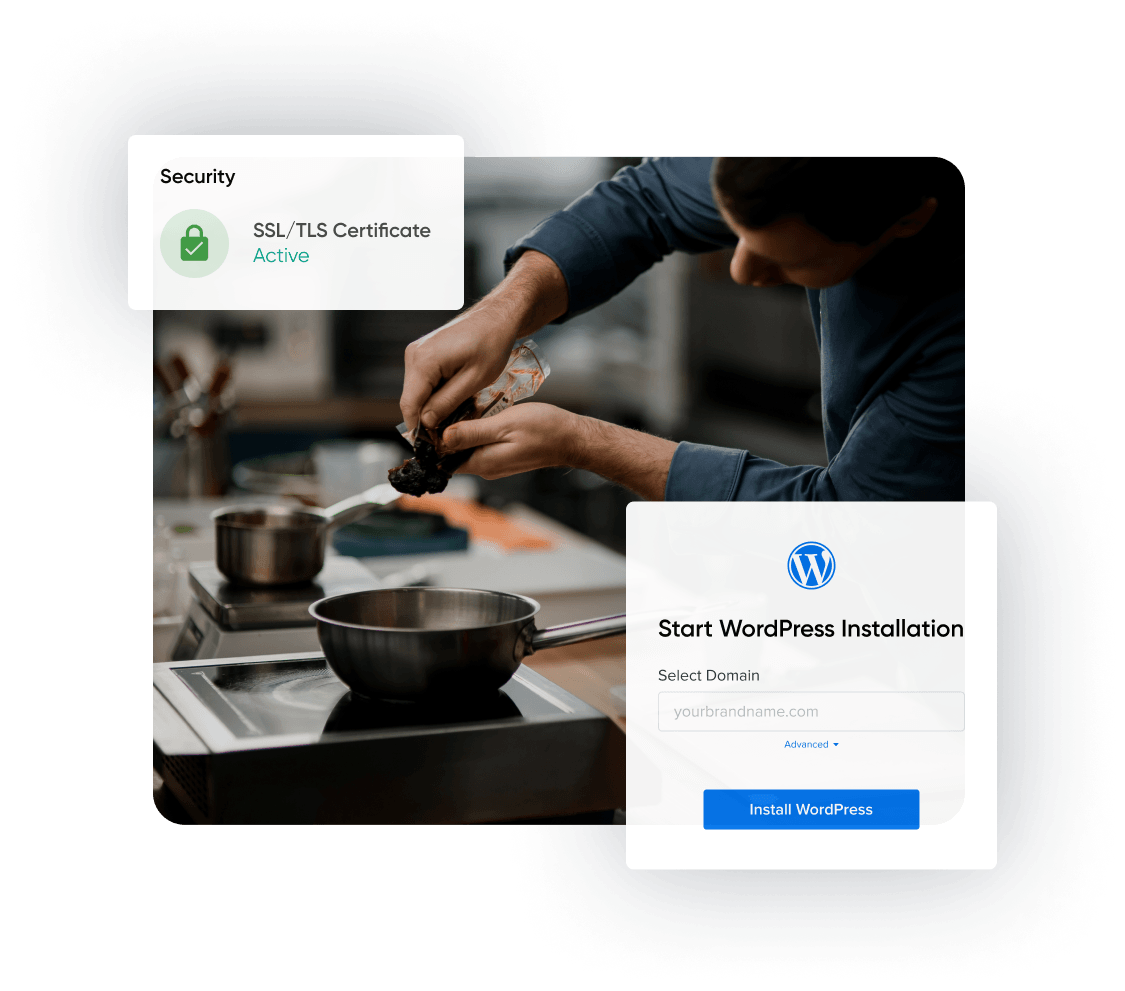
Experience enhanced site performance and security
Powered by NGINX, a powerful web server with advanced caching capabilities, DreamPress can significantly boost your site's security, speed, and responsiveness, creating a seamless experience for your visitors during periods of high traffic.
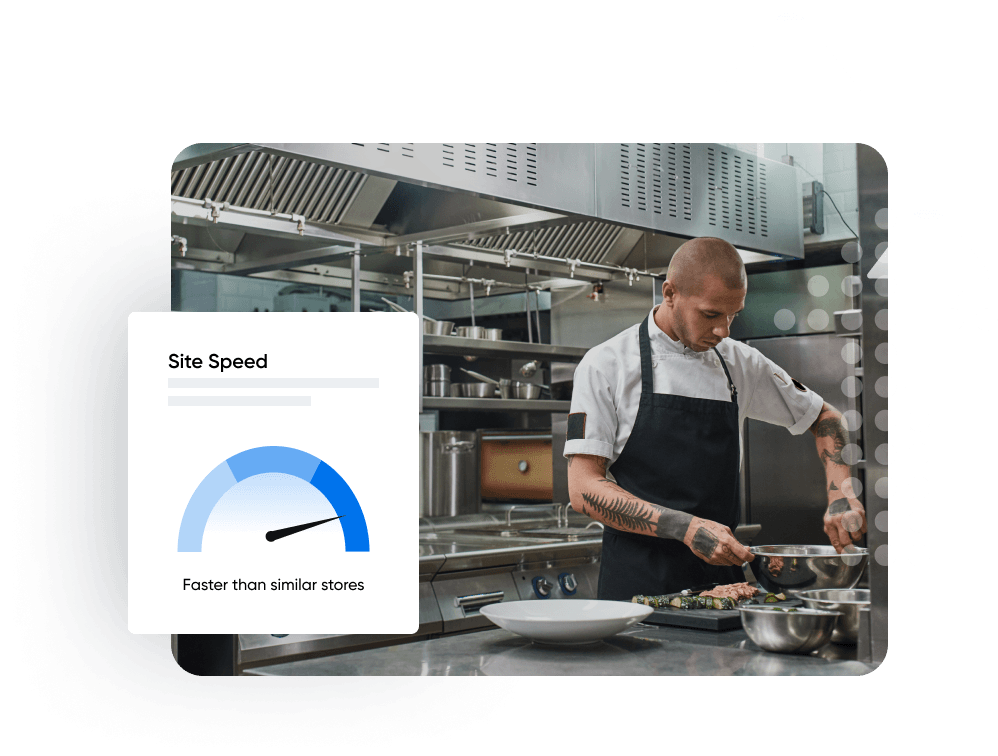
Create a beautiful website easily
Get your business online fast and make a good impression with customers. All DreamPress plans include access to a quickstart wizard, 200+ design themes, and a drag-and-drop editor to make getting started and managing your site simple.
See WP Site Builder Themes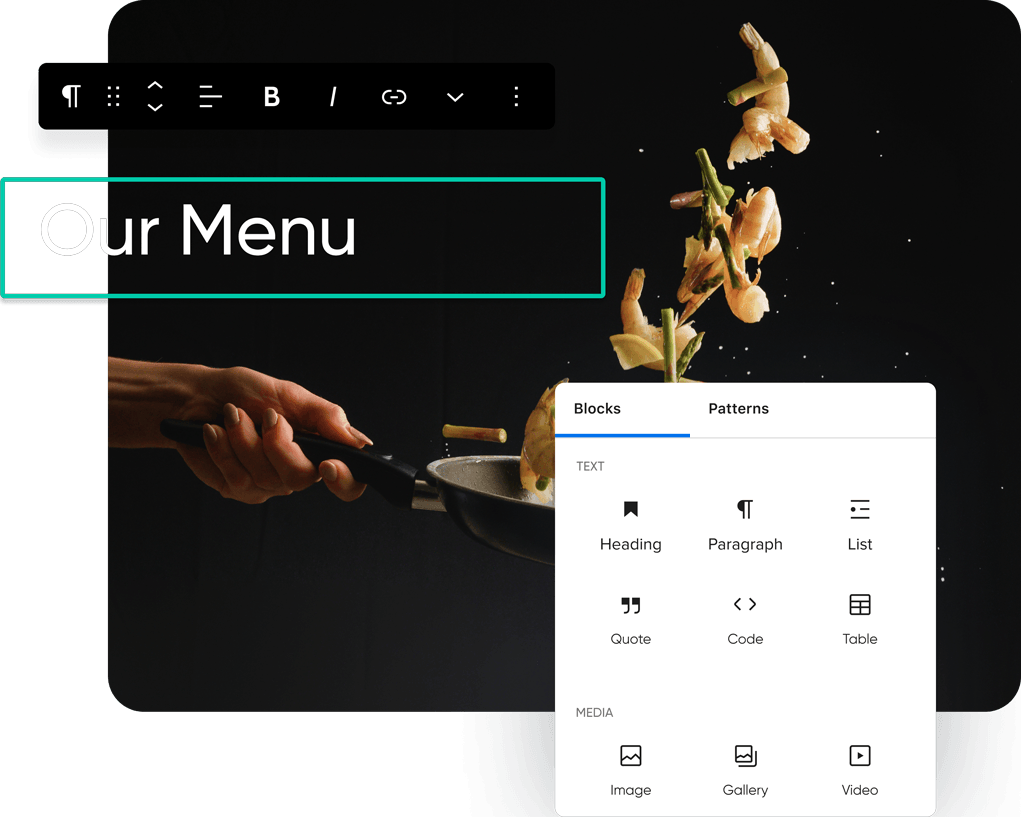
Premium support, at your service
With DreamPress you automatically get help from our highly-trained WordPress team, any time of the day. Now any problems you run into with your site are that much easier and faster to solve.
Pick the DreamPress Plan That's Best for You
Features | DreamPress $19.95/mo Promotional Pricing DisclaimerThis promotional offer is only available for new account registrations. This product has an introductory price of $19.95/mo which will last for 3 months. At the end of this introductory period, the price renews at the then-current rate (currently $23.99/mo). Get DreamPress | DreamPress Plus $29.95/mo Promotional Pricing DisclaimerThis promotional offer is only available for new account registrations. This product has an introductory price of $29.95/mo which will last for 3 months. At the end of this introductory period, the price renews at the then-current rate (currently $34.99/mo). Get DreamPress Plus | DreamPress Pro $79.95/mo Promotional Pricing DisclaimerThis promotional offer is only available for new account registrations. This product has an introductory price of $79.95/mo which will last for 3 months. At the end of this introductory period, the price renews at the then-current rate (currently $89.99/mo). Get DreamPress Pro |
|---|---|---|---|
| Server Environment | High-performance cloud | High-performance cloud | High-performance cloud |
| Resources | DreamPress ensures your resources are yours alone. By not sharing resources it means other users never affect your website’s performance. | DreamPress ensures your resources are yours alone. By not sharing resources it means other users never affect your website’s performance. | DreamPress ensures your resources are yours alone. By not sharing resources it means other users never affect your website’s performance. |
| # of WordPress Sites | 1 | 1 | 1 |
These levels are recommendations based on the number of monthly visitors accessing content on your site that are not served from cache. We will not cap your visits or charge overage fees, but excessive traffic of this nature can impact the performance of your site. | High | High | High |
Visits served from cache are not metered on any DreamHost plans. By default, DreamPress plans includes built-in caching to reduce the load of uncached visits and without the need to add any caching plugins to your site yourself. | Unmetered | Unmetered | Unmetered |
| Bandwidth | Unmetered | Unmetered | Unmetered |
| SSD Storage | 30GB | 60GB | 120GB |
Wordpress InstallerWe install WordPress so you don't have to. | |||
Create a staging site with just one click and safely test new plugins, themes, and code before pushing your changes live. | |||
NGINX is a robust web server known for its high performance and ability to handle large numbers of concurrent connections with minimal memory usage, making it ideal for serving static content and efficiently managing web traffic. | |||
Our experts will move your website without any interruptions in service. This priority migration service costs $199 per site, but it’s included for free with any DreamPress plan. | |||
Server-level caching can dramatically increase the speed and performance of your WordPress site. It's conveniently built into all DreamPress plans so you don't need to install any additional caching plugins. | |||
Easily migrate your existing WordPress site over to DreamHost using the free DreamHost Automated Migration plugin. | |||
The simplest way to create a beautiful WordPress website. Get your idea online today with an easy site creation wizard, free professional templates, and a drag-and-drop editor. | |||
Ensure a secure connection when visitors are on your site with a trusted and free SSL certificate from Let's Encrypt. | Pre-installed | Pre-installed | Pre-installed |
| Automatic WordPress Updates: Core & Security | |||
| Pre-Installed | Pre-Installed | Pre-Installed | |
| Automated Daily Backups | |||
| On-Demand Backups & 1-Click Restore | |||
In order to qualify for one free domain registration credit for the first full year, you must sign up for a 1-year or 3-year annual plan on Shared Starter, Shared Unlimited, or any annual DreamPress plan (monthly Shared or monthly DreamPress plans do not apply). This free credit is NOT available under any other hosting plan. You must also use the free registration within the first 3 months of your annual Shared/DreamPress plan. If you do not use the free registration within the first 3 months, then it's no longer available to use. Monthly plans do not apply. Offer valid for specific TLDs listed in the following article:Read More | |||
| Free Domain Privacy | |||
| Email Accounts @ Your Domain | |||
| Custom-built Control Panel | |||
| Advanced Features: SFTP, Shell Access, WP-CLI & more! | |||
| Support | WordPress Specialized | WordPress Specialized | WordPress Specialized |
| 24/7 Ticket Support | |||
| Live Chat Support | |||
| Phone Support Callbacks | Available | 3 | 5 |
It's our commitment to provide all DreamHost customers with fast and knowledgeable support. Priority Support, included with DreamPress Pro, is designed for customers that need an even higher level of hands-on experience. Priority Support includes expedited support, proactive monitoring, and advanced troubleshooting. | |||
DreamHost offers a full refund on Shared hosting fees if your plan is canceled within the first 97 days of opening the account. DreamPress hosting fees can be refunded within the first 30 days of opening the account. |

Hire a Pro, We'll Do
the Work for You
Ready to move faster?
We make it easy to tap into 20+ years of experience – our web experts will tackle whatever you need for a successful site.
Need something different?
Check out Shared Hosting – the most affordable way to get all the basics for your online business or blog.
Need Some Help?
Whether you're stuck or just want some tips on where to start, hit up our experts anytime. We're here to help!
DreamHost Sales Help
24/7/365 Through the Chat Widget
Customer Support Chat
24/7/365 Through the Panel
Customer Support Email
24/7/365 Through the Panel